The Canadian Privacy Law Blog: Developments in privacy law and writings of a Canadian privacy lawyer, containing information related to the Personal Information Protection and Electronic Documents Act (aka PIPEDA) and other Canadian and international laws.
Recent Posts
- This blog has moved
- Some thoughts on street photography
- RCMP changes rules for criminal records checks
- Saskatchewan amends privacy regs to permit solicia...
- US Federal judge declares warrantless wiretapping ...
- Commisser releases discussion paper on cloud compu...
- Heathrow worker given police warning for body scan...
- How Privacy Vanishes Online, a Bit at a Time
- Facebook plans to allow users to "share" location
- Drawing the curtain on ISP cooperation with law en...
On Twitter
About this page and the author
 The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
For full contact information and a brief bio, please see David's profile.
Please note that I am only able to provide legal advice to clients. I am not able to provide free legal advice. Any unsolicited information sent to David Fraser cannot be considered to be solicitor-client privileged.
Privacy Calendar
Archives
- January 2004
- February 2004
- March 2004
- April 2004
- May 2004
- June 2004
- July 2004
- August 2004
- September 2004
- October 2004
- November 2004
- December 2004
- January 2005
- February 2005
- March 2005
- April 2005
- May 2005
- June 2005
- July 2005
- August 2005
- September 2005
- October 2005
- November 2005
- December 2005
- January 2006
- February 2006
- March 2006
- April 2006
- May 2006
- June 2006
- July 2006
- August 2006
- September 2006
- October 2006
- November 2006
- December 2006
- January 2007
- February 2007
- March 2007
- April 2007
- May 2007
- June 2007
- July 2007
- August 2007
- September 2007
- October 2007
- November 2007
- December 2007
- January 2008
- February 2008
- March 2008
- April 2008
- May 2008
- June 2008
- July 2008
- August 2008
- September 2008
- October 2008
- November 2008
- December 2008
- January 2009
- February 2009
- March 2009
- April 2009
- May 2009
- June 2009
- July 2009
- August 2009
- September 2009
- October 2009
- November 2009
- December 2009
- January 2010
- February 2010
- March 2010
- April 2010
Links


Blogs I Follow
Small Print
The views expressed herein are solely the author's and should not be attributed to his employer or clients. Any postings on legal issues are provided as a public service, and do not constitute solicitation or provision of legal advice. The author makes no claims, promises or guarantees about the accuracy, completeness, or adequacy of the information contained herein or linked to. Nothing herein should be used as a substitute for the advice of competent counsel.
This web site is presented for informational purposes only. These materials do not constitute legal advice and do not create a solicitor-client relationship between you and David T.S. Fraser. If you are seeking specific advice related to Canadian privacy law or PIPEDA, contact the author, David T.S. Fraser.
Wednesday, February 28, 2007
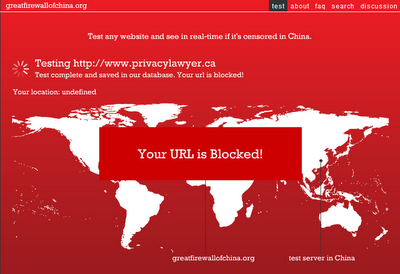
Blocked! By the Great Firewall of China
I don't know if I should be offended or flattered that this blog is blocked by the Great Firewall of China.
Check out the status of your URL here: http://www.greatfirewallofchina.org/test/.
Alberta Commissioner Order about journalistic collection and disclosure of personal information
The Information and Privacy Commissioner of Alberta just released a new Order in which the he determined he did not have jurisidction because the personal information in question was collected and disclosed for journalistic purposes, which is excluded from the purview of the Personal Information Protection Act.
Order P2005-004Summary: The Complainant alleged that the Organization had disclosed the Complainant's personal information when it published a newspaper article. The Organization argued that the disclosure of personal information in the form of a newspaper article was for journalistic purposes only as provided for by section 4(3)(c) of the Personal Information Protection Act. As such the Act did not apply to the personal information in question. The Commissioner decided the personal information disclosed were materials written for publication in the media and therefore collected and disclosed for journalistic purposes only in accordance with section 4(3)(c). The Commissioner, having determined that he had no jurisdiction in the matter, further stated that he had no authority to determine the remaining issue of the inquiry, regarding the allocation of a complainant's burden of proof.
Monday, February 26, 2007
Prison time under UK Data Protection Act?
DP Thinker is reporting on his blog that the UK Government intends to add prison time to the penalties available for misuse of personal information in the UK Data Protection Act: DP thinker: Data Protection Act 1998.
New findings from the Office of the Privacy Commissioner of Canada
A bunch of new findings have been released on the Privacy Commissioner's website recently:
Commissioner's Findings - Privacy Commissioner of Canada
- PIPEDA Case summary #364: Employer agrees to revise language of consent form regarding exchange of health information
- PIPEDA Case summary #363: Registrar collects personal information to combat domain name hijacking
- PIPEDA Case summary #362: Insurance adjuster readjusts its collection practices
- PIPEDA Case summary #361: Retailer requires photo identification to exchange an item
- PIPEDA Case summary #360: Bank erroneously e-mails employees’ personal information to client
- PIPEDA Case summary #359: Bank reported accurate information regarding bounced cheque
- PIPEDA Case summary #358: Individual objects to insurance company’s consent requirements
- PIPEDA Case summary #357: Inconclusive evidence of disclosure prompts fitness club to clarify privacy policy for clients and staff
- PIPEDA Case summary #356: Customer’s banking personal information found in a recycling bin
- PIPEDA Case summary #355: Funeral home’s disclosure in pursuit of a debt allowed under the Act
- PIPEDA Case summary #354: Fees for access questioned
- PIPEDA Case summary #353: Bank’s Ombudsman revises agreement to clearly explain exchanges of personal information between it and the bank
Labels: health information, pipeda findings, privacy
Saturday, February 24, 2007
Commissioner pressured bank to go public on data loss
Labels: breach notification, privacy
RCMP seeks easier access to personal information
The Parliamentary Committee on Access to Information, Privacy and Ethics continues its five year review of PIPEDA, most recently hearing from the Royal Canadian Mounted Police on Tuesday and the Privacy Commissioner on Wednesday.
The RCMP is calling for lowering the bar in PIPEDA to allow greater access to personal information in the course of investigations. The Act, as it is currently in force, allows organizations to provide personal information without consent to law enforcement in certain circumstances. Section 7(3)(c.1)(iii) of PIPEDA allows this, but only where the law enforcement agency has "lawful authority to obtain the information":
Disclosure without knowledge or consent(3) For the purpose of clause 4.3 of Schedule 1, and despite the note that accompanies that clause, an organization may disclose personal information without the knowledge or consent of the individual only if the disclosure is ...
(c.1) made to a government institution or part of a government institution that has made a request for the information, identified its lawful authority to obtain the information and indicated that(i) it suspects that the information relates to national security, the defence of Canada or the conduct of international affairs,(ii) the disclosure is requested for the purpose of enforcing any law of Canada, a province or a foreign jurisdiction, carrying out an investigation relating to the enforcement of any such law or gathering intelligence for the purpose of enforcing any such law, or
(iii) the disclosure is requested for the purpose of administering any law of Canada or a province;
Representatives of the RCMP told the committee this requirement is the force's largest single impediment in child exploitation investigations. The force would like the ability to get pesonal information even in circumstances where they don't have enough to justify a warrant.
The Privacy Commissioner is not at all impressed.
For media coveage, see: Federal watchdog and RCMP battle privacy protection.
And for some earlier discussions on this and related topics, see label:warrants.
Labels: law enforcement, lawful authority, national security, privacy, warrants
Wednesday, February 21, 2007
T.J. Maxx probe finds broader hacking
This isn't good:
T.J. Maxx probe finds broader hacking | Tech News on ZDNetThe TJX Companies, the discount retailer best known for its T.J. Maxx and Marshalls clothing stores, said Wednesday that its hacking investigation has uncovered more extensive exposure of credit and debit card data than it previously believed.
Information on millions of TJX customers may have been exposed in the long-running attack, which was made public last month. It affects customers of any of TJX store in the U.S., Canada or Puerto Rico, with the exception of its Bob's Stores chain.
The breach of credit and debit card data was initially thought to have lasted from May 2006 to January. However, TJX said Wednesday that it now believes those computer systems were first compromised in July 2005.
TJX said credit and debit card data from January 2003 through June 2004 was compromised. The company previously said that only 2003 data may have been accessed. According to TJX, however, some of the card information from September 2003 through June 2004 was masked at the time of the transactions.
The company added that names and addresses apparently were not included with the card information, that debit card PIN numbers are not believed to have been vulnerable, and that data from transactions made with debit cards issued by Canadian banks likely were not vulnerable.
TJX also found that there was evidence of intrusion into the system that handles customer transactions for its T.K. Maxx stores in the United Kingdom and Ireland, but that there has been no confirmation that anyone actually accessed that data.
In addition to these exposures, TJX said there were more breaches of driver's license information than it previously thought. These included the license numbers, names and addresses of customers making merchandise returns in the U.S. and Puerto Rico locations of T.J. Maxx, Marshalls and HomeGoods stores. That compromised data, according to TJX, is restricted to returns without receipts that took place in the last four months of 2003, as well as in May 2004 and June 2004.
TJX plans to notify customers whose driver's license data may have been accessed.
The company, which is continuing its investigation, encourages customers to check their credit-card and bank-account records and look for further updates on its website.
Labels: cardsystems, privacy, retail, tjx
Sunday, February 18, 2007
Kids, the Internet, and the End of Privacy: The Greatest Generation Gap Since Rock and Roll
 Last night, I went to a party for a colleague celebrating her 36th birthday. The theme was pretty clever: to celebrate the tewentieth anniversary of her sweet sixteen. Guests were encouraged to wear their best '80s outfits. A number did and the outfits were classic. With MC Hammer blaring in the bar, there was some reminiscing about the teen years, twenty years ago.
Last night, I went to a party for a colleague celebrating her 36th birthday. The theme was pretty clever: to celebrate the tewentieth anniversary of her sweet sixteen. Guests were encouraged to wear their best '80s outfits. A number did and the outfits were classic. With MC Hammer blaring in the bar, there was some reminiscing about the teen years, twenty years ago. My generation is very different from those currently going through their teen years. I have to go down to the basement and open a trunk to find all the pictures that I took during those years. Many current teens just need to log into Myspace, Friendster, Flickr or pull up their blogs to find the full, detailed chronicle of their adolescence.
I'm a different person from who I was twenty years ago. I don't think I'd want to have that time of huge changes and wholesale weirdness on the 'net for all to see. (At the time I might have thought it was cool, but in retrospect .... not so much.)
Last week's New York magazine has a very interesting, feature length article on current teens and how their experiences are chronicled in great detail on the internet. Much of it deals with ADHD type attention spans and attention whoring, but the perception of privacy is very interesting.
Kids, the Internet, and the End of Privacy: The Greatest Generation Gap Since Rock and Roll -- New York MagazineKids today. They have no sense of shame. They have no sense of privacy. They are show-offs, fame whores, pornographic little loons who post their diaries, their phone numbers, their stupid poetry—for God’s sake, their dirty photos!—online. They have virtual friends instead of real ones. They talk in illiterate instant messages. They are interested only in attention—and yet they have zero attention span, flitting like hummingbirds from one virtual stage to another.
But maybe it’s a cheap shot to talk about reality television and Paris Hilton. Because what we’re discussing is something more radical if only because it is more ordinary: the fact that we are in the sticky center of a vast psychological experiment, one that’s only just begun to show results. More young people are putting more personal information out in public than any older person ever would—and yet they seem mysteriously healthy and normal, save for an entirely different definition of privacy. From their perspective, it’s the extreme caution of the earlier generation that’s the narcissistic thing. Or, as Kitty put it to me, “Why not? What’s the worst that’s going to happen? Twenty years down the road, someone’s gonna find your picture? Just make sure it’s a great picture.”
And after all, there is another way to look at this shift. Younger people, one could point out, are the only ones for whom it seems to have sunk in that the idea of a truly private life is already an illusion. Every street in New York has a surveillance camera. Each time you swipe your debit card at Duane Reade or use your MetroCard, that transaction is tracked. Your employer owns your e-mails. The NSA owns your phone calls. Your life is being lived in public whether you choose to acknowledge it or not.
So it may be time to consider the possibility that young people who behave as if privacy doesn’t exist are actually the sane people, not the insane ones. For someone like me, who grew up sealing my diary with a literal lock, this may be tough to accept. But under current circumstances, a defiant belief in holding things close to your chest might not be high-minded. It might be an artifact—quaint and naïve, like a determined faith that virginity keeps ladies pure. Or at least that might be true for someone who has grown up “putting themselves out there” and found that the benefits of being transparent make the risks worth it.
Labels: health information, privacy, surveillance
Saturday, February 17, 2007
Mining drivers' licence databases raises privacy concerns
Yesterday's New York Times ran an interesting article on the increasing application of biometrics to drivers' licenses in the United States, and the collateral use of this technology. For example, photos from state databases are run against the rest of the database to identify those who have multiple licenses (to try to thwart a license suspension) or against photos of wanted felons. This practice has privacy advocates upset:
Driver’s License Emerges as Crime-Fighting Tool, but Privacy Advocates Worry - New York Times“What is the D.M.V.?” asked Lee Tien, a lawyer with the Electronic Frontier Foundation and a privacy advocate. “Does it license motor vehicles and drivers? Or is it really an identification arm of law enforcement?”
Anne L. Collins, the Massachusetts registrar of motor vehicles, said that people seeking a driver’s license at least implicitly consent to allowing their images to be used for other purposes.
“One of the things a driver’s license has become,” Ms. Collins said, “is evidence that you are who you say you are.”
Labels: biometrics, privacy
Friday, February 16, 2007
US Federal Court limits police surveillance of protests
A federal court judge in New York has delivered a strong rejection the practice of routine law enforcement video taping of protests unless there is actual reason to believe that illegal acts will be comitted.
Judge Limits New York Police Taping - New York TimesIn a rebuke of a surveillance practice greatly expanded by the New York Police Department after the Sept. 11 attacks, a federal judge ruled yesterday that the police must stop the routine videotaping of people at public gatherings unless there is an indication that unlawful activity may occur.
Four years ago, at the request of the city, the same judge, Charles S. Haight Jr., gave the police greater authority to investigate political, social and religious groups.
In yesterday’s ruling, Judge Haight, of United States District Court in Manhattan, found that by videotaping people who were exercising their right to free speech and breaking no laws, the Police Department had ignored the milder limits he had imposed on it in 2003....
Related
- Text of the Decision (pdf)
- The Empire Zone Blog: Court Case Primeval
- Police Infiltrate Protests, Videotapes Show (Dec. 22, 2005)
- Video: N.Y.C. Police Surveillance
From Boing Boing.
Labels: privacy, surveillance, video surveillance
Thursday, February 15, 2007
Taking care of business with the four Ps
Dawn Jutla of the Saint Mary's Sobey School of Business has a piece in today's Chronicle Herald on information protection that's worth a read:
The ChronicleHerald.caMinding your Ps can protect your customers
By DAWN JUTLA / Taking Care of Business
IN 2006, the FBI reported that unauthorized data access — similar to the problem faced by WINNERS’ parent company T.J. Max — became the second-most-costly loss in organizations due to computer crime after viruses. As the costs of unauthorized access are on the rise, suppliers will increasingly be asked to provide copies of their security and privacy policies and processes as part of contract agreements.
Security and privacy documents are key communication vehicles for helping employees understand and comply with recommended security and privacy guidelines, as well as learn good security and privacy behaviours. Recent high-profile examples of where policies were not well-formulated, communicated or complied with include AOL’s firing of its chief technology officer after users’ search results were published on the web, and Boeing’s disclosure that the personal information of hundreds of thousands of current and former employees was compromised when an unencrypted laptop was stolen from an employee’s car.
To control unauthorized access from insiders and outsiders, good security policies, at a minimum, address the management of four Ps: Policy guidelines for employees, Patches and updates, Protective software and devices, and Physical security. Security managers, chief information officers and consultants help company executives understand the costs and benefits of the 4Ps. ...
Policy guidelines for employees: ...
Patches and updates: ...
Protective software and devices: ...
Physical security: ....
Dawn Jutla is an associate professor in the department of finance, information systems and management science. Taking Care of Business is a monthly column created by the Sobey School of Business.
Labels: laptop, law enforcement, privacy
Wednesday, February 14, 2007
US DoD to require suppliers to use RFID
The United States Department of Defence is requiring suppliers of some commodities to use passive RFID chips to identify and inventory supplies. From Cryptome: DoD Final Rule on RFID Spy Chips.
Monday, February 12, 2007
Alberta Commissioner's office faults EAP provider
Released today from the Information and Privacy Commissioner of Alberta:
Employee Assistance Provider found in contravention of Personal Information Protection ActThe Office of the Information and Privacy Commissioner has found that Wilson Banwell Human Solutions Inc. (Wilson Banwell) contravened the Personal Information Protection Act (PIPA) by disclosing more personal information than was necessary to a complainant's employer. The investigation also determined Wilson Banwell contravened PIPA by disclosing the complainant's personal information to a union for purposes that were not reasonable, and to an extent that was not reasonable.
After failing to pass a drug and alcohol test, the complainant was referred to Wilson Banwell, an Employee Assistance Provider (EAP), for a "return to work assessment." He signed a consent authorizing release of "assessment / treatment summaries" to his employer to facilitate his return to work. The complainant believed Wilson Banwell would limit its report to recommendations arising from the assessment. However, the Wilson Banwell psychologist sent a three-page report to both the complainant's employer and union. The report provided a summary of the clinical interview the psychologist conducted with the complainant, including details of a previous visit the complainant had made to Wilson Banwell on his own initiative, and some personal information of the complainant's wife.
The Investigator recommended Wilson Banwell:
- revise its "Release of Information" form to clarify exactly what information will be disclosed to a client's employer for return to work purposes, and
- remind all staff of Wilson Banwell's policies respecting written consent, and the requirement to disclose only the least amount of information necessary for reasonable purposes.
Wilson Banwell agreed to implement these recommendations.
For more information about investigation report P2007-IR-001, please visit our website at: http://www.oipc.ab.ca/
I expect the result would have been the same if the complaint was brought under PIPEDA, except the parties wouldn't have been named.
Thursday, February 08, 2007
Finding the smoking gun in security breaches
In most cases of fraud following a security breach, the biggest problem for consumers seeking a remedy is proving the connection between the breach and the ensuing fraud. According to CIO Blogs, the TJX breach is different and a small bank in New England has made the connection. It has found the smoking gun and says it will seek damages against the company.
This may be the wakeup call that will force companies to be more diligent about security. See: CIO Blogs - The TJX security breach. This one's different. Way different. |.
Thanks to John Gregory for the link.
Labels: fraud, identity theft, privacy, tjx, tort
Recruiting software company sets up data centre in Canada to address Patriot Act concerns
This is the first public announcement of the establishment of a data centre in Canada in response to privacy concerns about data being hosted in the United States:
Cytiva Responds to Canadian Privacy Concerns With New Canadian Data Centre: Financial News - Yahoo! FinanceWednesday February 7, 9:00 am ET
New Data Centre Helps Canadian Employers Comply With Privacy Laws and Addresses Concerns About the United States Patriot Act
VANCOUVER, BC--(MARKET WIRE)--Feb 7, 2007 -- Cytiva Software Inc. (CDNX:CRX.V - News), a leading provider of on-demand recruiting software solutions, announced today the establishment of a new data centre located in Burnaby, BC. This new data centre provides Canadian clients of Cytiva's SonicRecruit recruiting software with assurance that their candidate and employee data will remain in Canada. This is important news for Canadian companies trying to comply with privacy laws. A growing number are concerned about their employee data being subject to a United States Patriot Act that lessens requirements for government seizure of personal data in U.S. territories.
Because of the Personal Information Protection and Electronic Documents Act (PIPEDA), and other provincial privacy laws, Canadian companies that use software from U.S. companies to manage their recruiting and other human resource processes face a complicated landscape in trying to protect employee data. When employee data is transferred outside of Canada to U.S. servers that run on-demand human resources software, the issue becomes even more complicated. This data may become subject to the United States Patriot Act, which supersedes PIPEDA inside the U.S.
Canadian privacy laws are some of the most stringent in the world and have been evolving rapidly over the last ten years. All this has compelled many Canadian companies to require that their customer and employee data stay in Canada.
"Some vendors walk away from Canadian business, while others try and deal with the issue through contractual language regarding privacy," said Jason Moreau, president and CEO of Cytiva Software. "But Cytiva recognizes how important an issue this is to Canadian companies, so we have taken the extra step of establishing a data centre on Canadian soil."
The Burnaby BC data centre provides state-of-the-art security, network access, climate control and power backup.
Cytiva announces the establishment of the Canadian data centre a few months after implementing a host-based Intrusion Protection System (IPS) which goes beyond mere firewalls or detection systems and provides the highest level of data protection available.
"With the Intrusion Protection System and the option of local hosting for our Canadian clients, Cytiva sets the standard for privacy and data protection for on-demand recruiting software," says Moreau. "We believe that all companies should expect this level of protection."
About Cytiva Software Inc.
Cytiva Software Inc. (CDNX:CRX.V - News) provides innovative recruiting software and services to mid-sized and Fortune 500 companies. More than an application, its flagship talent acquisition product, SonicRecruit, allows corporations to screen applicants, automate their recruiting departments, customize their corporate career sites and hire great people. This premier applicant tracking system improves recruiting effectiveness, speeding up the hiring process and reducing cost per hire. For more information, visit http://www.sonicrecruit.com
The TSX has not reviewed and does not accept responsibility for the accuracy or adequacy of this news release, which has been prepared by management.
Distributed by Filing Services Canada and retransmitted by Market Wire
Labels: outsourcing, patriot act, privacy
Call for a privacy law in Thailand
The Managing Director of Oracle ASEAN is calling on the Thai government to pass a strong privacy law so that Thailand will not be left behind in the BPO boom:
Bangkok Post : We need data privacy act to attract BPO:"Thailand needs to quickly pass the Data Privacy Act if it is to avoid being left out of the world's IT and business process outsourcing (BPO) boom, according to Natasak Rodjanapiches, managing director of Oracle ASEAN.
Other requirements include a need for strong security standards, interoperability standards as well as the legal and privacy frameworks that are needed for a knowledge-based industry to flourish.
'Nobody will feel secure outsourcing to Thailand if the legal and privacy framework is still so uncertain. The interim government has an opportunity to do something good for the industry now by passing this law quickly,' he said. ..."
Labels: outsourcing, privacy
Tuesday, February 06, 2007
OPC fact sheet on PIAs
The Office of the Privacy Commissioner of Canada has released its most recent fact sheet. This one's a thumbnail sketch of privacy impact assessments. See: Fact Sheet: Privacy Impact Assessments (February 2007).
Labels: privacy
Federal Court orders Privacy Commissioner to investigate American company
Yesterday, the Federal Court of Canada released what is an important decision related to the jurisdiction of the Federal Privacy Commissioner to investigate organizations outside of Canada, but are trafficking in the personal information of Canadians. Phillipa Lawson, of the University of Ontario, filed a complaint against Abika.com after she ordered, paid for and obtained her own personal information from the information broker. She then complained to the Privacy Commissioner of Canada under PIPEDA. The Commissioner declined to investigate saying that the legislation does not extend to investigating organizations located only in the United States.
Phillipa Lawson sought judicial review of the decision not to investigate and the Federal Court agreed. It concluded that the Privacy Commissioner confused her power to investigate with the effectiveness of the investigation. (Abika refused to participate in the investigation.)
The conclusion of the decision says it all: "In conclusion, PIPEDA gives the Privacy Commissioner jurisdiction to investigate complaints relating to the transborder flow of personal information."
Thanks to Michael Geist for the link.
For additional background, see here.
Labels: privacy
Monday, February 05, 2007
No sneaky PC searches in Germany
Labels: europe, law enforcement, privacy, warrants
VeriChip goes public
Labels: biometrics, privacy, rfid
Sunday, February 04, 2007
Gov't balks at phone privacy provision
The Federal Communications Commission is trying to develop rules to counter pretexting, but is encountering resistance from the FBI and Secret Service. A requirement to destroy calling records after they have served legitimate business purposes would not make the records available to be reviewed by law enforcement. A second requirement to notify consumers if their records have been disclosed by a pretexter would tip the consumers off if they are the subject of an investigation. See: Gov't balks at phone privacy provision - Yahoo! News.
Labels: law enforcement, national security, pretexting, privacy
Consumer response and responsibility
Dissent, at the Chronicles of Dissent (part of Pogowasright) asks whether consumer stupidity plays a role in privacy breaches and the response. Dissent points to an article from my local newspaper, the Chronicle Herald, quoted below.
I can't say that Canadians are more prudent or insistent about their privacy than our cousins below the border, or more stupid. In my experience on the east coast of Canada, most folks around here are much more trusting of the companies they do business with. The cynicism from down south hasn't quite permeated this neck of the woods. One thing we generally are more tolerant of is government regulation, such as that governing privacy.
We have not yet seen any provinces or the federal government come up with mandatory breach notification, with the narrow exception contained in Ontario's health privacy law. In that regard, we are lagging behind most of the states in the US.
Winners reassures CanadiansSecurity breach did not involve cards issued north of border, says retailer
By AMANDA-MARIE QUINTINO The Canadian Press
TORONTO — Assurances from Winners and HomeSense that a security breach reported last month did not involve Canadian debit-card transactions isn’t making much of dent with customers of the two retail chains.
Not much can keep them from their bargain hunting.
The deals to be found at Winners makes the risk of becoming the victim of credit card fraud worthwhile, said Sherry Croney as she slowly sifted through the blouse racks at one of the chain’s cavernous stores in downtown Toronto.
Croney said she never uses her credit card when clothes shopping, and even if she did, a security breach wouldn’t stop her.
...
"Our computer security experts have now completed their investigation of the portion of our computer network that handles Winners and HomeSense transactions, and they have advised us that they do not believe that debit cards issued by Canadian banks were compromised in the intrusion," said a TJX statement posted on the Winners website.
I note there is only a reference to Canadian debit cards.... nothing said about credit cards.
Labels: breach notification, privacy, retail, tjx
Saturday, February 03, 2007
Behind the scenes in organized online fraud
Wired News recently ran a very interesting, multi-part series that provides a behind the scenes look at organized credit card fraud:
Wired News: I Was a Cybercrook for the FBIDavid Thomas ran one of the most popular online crime hubs, while the FBI ran him.
The Grifters operation makes headway against the notorious "King Arthur," the Moriarty of cybercrime.
A U.S. agent tells of the frustration of tracking Eastern European criminal masterminds.
The FBI shuts down its operation, as the Secret Service drops the hammer on the underground carding scene.
Labels: fraud, law enforcement, privacy
Incident: Veterans Affairs hard drive with personal data missing
The Associated Press is reporting that the US Department of Veterans Affairs has lost a portable hard-drive that contained unencrypted records of thousands of veterans. See: AP Wire | 02/03/2007 | VA hard drive with personal data missing.
Friday, February 02, 2007
PIPEDA Hearings - Days 9 and 10
The PIPEDA Review Hearings have resumed after a recess and Michael Geist continues to link to notes taken at the hearings (see: Michael Geist - PIPEDA Hearings - Days 9 (banking industry) and 10 (Chamber of Commerce, Insurance)). The focus has shifted to discussions of breach notification, a topic that now seems to have strong support on the committee.
Labels: breach notification, pipeda review, privacy
Thursday, February 01, 2007
Data Privacy Bill Expected to Target Retailers, Banks
According to the Washington Post, the new chairman of the House Financial Services Committee will be pushing hard for a national privacy/data breach law:
Data Privacy Bill Expected to Target Retailers, Banks - washingtonpost.comData Privacy Bill Expected to Target Retailers, Banks
By Brian Krebs
washingtonpost.com Staff Writer
Friday, February 2, 2007; Page D03
Data privacy is likely to be among the hottest technology issues to face Congress this year, in part due to interest from the new chairman of the House Financial Services Committee.
Panel Chairman Barney Frank (D-Mass.) said he plans to craft a bill that would exempt companies from disclosing data breaches, provided they secure the data with encryption software or other technology that would render it virtually unreadable if it fell into the wrong hands....
Citizen Journalism and Privacy
Teresa Scassa of Dalhousie Law School has an interesting contribution to blog*on*nymity about Citizen Journalism and Privacy.
Labels: privacy
![]()

The Canadian Privacy Law Blog is licensed under a
Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Canada License.