The Canadian Privacy Law Blog: Developments in privacy law and writings of a Canadian privacy lawyer, containing information related to the Personal Information Protection and Electronic Documents Act (aka PIPEDA) and other Canadian and international laws.
Recent Posts
- This blog has moved
- Some thoughts on street photography
- RCMP changes rules for criminal records checks
- Saskatchewan amends privacy regs to permit solicia...
- US Federal judge declares warrantless wiretapping ...
- Commisser releases discussion paper on cloud compu...
- Heathrow worker given police warning for body scan...
- How Privacy Vanishes Online, a Bit at a Time
- Facebook plans to allow users to "share" location
- Drawing the curtain on ISP cooperation with law en...
On Twitter
About this page and the author
 The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
For full contact information and a brief bio, please see David's profile.
Please note that I am only able to provide legal advice to clients. I am not able to provide free legal advice. Any unsolicited information sent to David Fraser cannot be considered to be solicitor-client privileged.
Privacy Calendar
Archives
- January 2004
- February 2004
- March 2004
- April 2004
- May 2004
- June 2004
- July 2004
- August 2004
- September 2004
- October 2004
- November 2004
- December 2004
- January 2005
- February 2005
- March 2005
- April 2005
- May 2005
- June 2005
- July 2005
- August 2005
- September 2005
- October 2005
- November 2005
- December 2005
- January 2006
- February 2006
- March 2006
- April 2006
- May 2006
- June 2006
- July 2006
- August 2006
- September 2006
- October 2006
- November 2006
- December 2006
- January 2007
- February 2007
- March 2007
- April 2007
- May 2007
- June 2007
- July 2007
- August 2007
- September 2007
- October 2007
- November 2007
- December 2007
- January 2008
- February 2008
- March 2008
- April 2008
- May 2008
- June 2008
- July 2008
- August 2008
- September 2008
- October 2008
- November 2008
- December 2008
- January 2009
- February 2009
- March 2009
- April 2009
- May 2009
- June 2009
- July 2009
- August 2009
- September 2009
- October 2009
- November 2009
- December 2009
- January 2010
- February 2010
- March 2010
- April 2010
Links


Blogs I Follow
Small Print
The views expressed herein are solely the author's and should not be attributed to his employer or clients. Any postings on legal issues are provided as a public service, and do not constitute solicitation or provision of legal advice. The author makes no claims, promises or guarantees about the accuracy, completeness, or adequacy of the information contained herein or linked to. Nothing herein should be used as a substitute for the advice of competent counsel.
This web site is presented for informational purposes only. These materials do not constitute legal advice and do not create a solicitor-client relationship between you and David T.S. Fraser. If you are seeking specific advice related to Canadian privacy law or PIPEDA, contact the author, David T.S. Fraser.
Friday, January 02, 2009
The Canadian Privacy Law Blog is Five!
 Five years ago, on January 2, 2004, a new age of privacy was creeping across Canada and this blog was born. The day before, at the stroke of midnight, the Personal Information Protection and Electronic Documents Act (Canada) had come fully into force. The Alberta and British Columbia Personal Information Protection Acts also became effective on the first day of 2004.
Five years ago, on January 2, 2004, a new age of privacy was creeping across Canada and this blog was born. The day before, at the stroke of midnight, the Personal Information Protection and Electronic Documents Act (Canada) had come fully into force. The Alberta and British Columbia Personal Information Protection Acts also became effective on the first day of 2004.
Since then, we have seen dramatic changes in privacy throughout the world: Identity theft is on the rise; there have been literally thousands of data breaches exposing the personal information of millions of people; governments are looking for easier access to personal information; video surveillance is more widespread; more personal information is generated digitally and aggregated in private hands.
And in the past year specifically, things have remained interesting on the privacy front. We've seen debate over changes to PIPEDA without anything definitive coming from the mandatory five year review. We've also seen arguments put forward to reform the public sector Privacy Act. Focus has also been drawn to the increasing practice of examining laptops at US border crossings. Litigation between Viacom and Google has raised awareness of log information that's often retained by internet companies. And Google has also been sued by a couple claiming their privacy has been violated by presenting pictures of their house in Google Street View. But in the last year, the one big privacy story that was supposed to have the largest impact on Canadians was the implementation of the National Do Not Call List. Whether it has, in fact, had an impact is the subject of debate.
I'd like to thank the many thousands of readers of the blog for visiting this site and thanks to those who have contacted me with comments, compliments, suggestions and links to interesting news. It's been a pleasure to write and I plan to keep it going as long as there's interesting privacy news to report.
Birthday cake graphic used under a creative commons license from K. Pierce.
Labels: border, dncl, google, google street view, identity theft, incident, laptop, lawful access, pipeda review, privacy, privacy act, telemarketing, video surveillance
Friday, October 10, 2008
Missing hard-drive in the UK contains info on 100K military personnel
Labels: breach notification, incident, privacy, uk
Thursday, April 17, 2008
Incident: Ontario patient files found in dumpster
The Ontario Information and Privacy Commissioner is investigating after old medical records were found in a dumpster behind a coffee shop by a retiree. The affected patients will have to be notified as the information is subject to PHIPA, which contains Canada's only mandatory breach notification. See: TheSpec.com - Local - St. Joe's patient files found in dumpster.
Labels: breach notification, health information, incident, ontario, phipa, privacy
Monday, April 07, 2008
Incident: Tax files, private info turn up in Vancouver dumpster
In case you needed further proof that you must shred all personal information that you're disposing. Loads of personal tax information has surfaced after a high-profile accountant in Vancouver chucked it into a locked dumpster outside his offices:
CTV British Columbia- Tax files, private info turn up in dumpster - CTV News, Shows and Sports -- Canadian Television... Many of the documents -- marked with phrases such as "personal and confidential" -- come from the office of Peter Roberts, a well-known accountant.
"Oh my gosh," said one of Roberts' clients, David Weinberg, whose name was on several files.
"I'll have him either return this to me or assure me that he will be changing his privacy practices going forward to assure that not just this but all of his clients' documents are properly shredded."
When reached by phone, Roberts said that he put a bag full of the documents in the dumpster on Saturday.
He said he doesn't own a shredder and believed the documents would be safe because the dumpster is secured by a padlock.
But to Vancouver's large and innovative homeless population, a lock isn't much of a safeguard....
Thanks to a regular reader from the west coast for pointing me to this incident.
Thursday, March 27, 2008
Info on participants in kids' summer program found in open trash in Toronto
The Toronto Sun is reporting that information about children who participated in a city-funded summer program was found in an open trash bin in a Toronto apartment building. The Sun also notes that a resident of the building was recently charged for child pornography offenses, but the two do not appear to be related.
TorontoSun.com - Toronto And GTA- Kids' data exposedDocuments containing detailed information on children who participated in a city-funded summer program were carelessly left out in the open at a public housing apartment building where a man was recently charged with possession of child pornography.
George Pappas, director of the Glamorgan Resident's Association, was running one of his weekly social events for the residents when he and another member of his group found approximately 200 pages near the top of a garbage can in the rec room.
The papers contained the birth dates, health card numbers, contact details and other personal information on children from 6 and 7 Glamorgan Ave. and other nearby Toronto Community Housing buildings who participated in the summer program. ...
Labels: health information, incident, ontario, privacy
Saturday, March 15, 2008
Illustration of ten largest data breaches since 2000
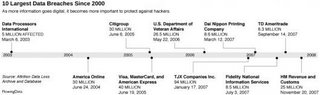 Flowing Data, which "explores how statisticians, designers, computer scientists, and others are using data to understand more about ourselves and our surroundings", has an illustration of the ten largest recent data breaches. See: 10 Largest Data Breaches Since 2000 - Millions Affected FlowingData. Via Boing Boing.
Flowing Data, which "explores how statisticians, designers, computer scientists, and others are using data to understand more about ourselves and our surroundings", has an illustration of the ten largest recent data breaches. See: 10 Largest Data Breaches Since 2000 - Millions Affected FlowingData. Via Boing Boing.
Sunday, January 20, 2008
Incident: Personal info on 600K UK military recruits on stolen laptop
The Register reports that a laptop containing the personal information of 600,000 UK military recruits was on a laptop stolen from a naval officer's car. See: Join the army, get your ID pinched - MoD laptop goes AWOL | The Register.
Thursday, January 10, 2008
Security breach at the Canadian Bar Association
The Canadian Bar Association advises that it has noted "unauthorized activity" related to member information: CBA Personal Information Advisory.
Michael Geist quotes from the notification the CBA has sent to affected members:
Michael Geist - Canadian Bar Association Hit By Security BreachYour records may have been affected by this unauthorized activity. The files contained personal information relating to online orders (name, address, phone, fax, member number) and encrypted credit card information. We have no reason to believe that the encrypted credit card information was compromised. CBA uses one of the most secure encryption solutions available to protect credit card information. As a precautionary measure, we recommend that members monitor their credit card accounts for suspicious activity.
Labels: breach notification, incident, privacy
Tuesday, January 01, 2008
New breach blog
Emergent Chaos is linking to a reasonably new resource, the Breach Blog, that contains data on personal information breaches, similar to Pogo's and the Attrition.org Data Loss Archive and Database (DLDOS).
I've stopped blogging about most breaches, primiarily because they are too numerous and others can provide that service. I try, however, to keep on top of them and report on those that are particularly newsworthy or provide novel lessons to be learned. I'll certainly add it to my blogroll.
Friday, December 28, 2007
Security breach affects hundreds of thousands of porn consumers
Personal information on hundreds of thousands of users of adult websites may have been compromised in a breach that is said to have the potential to undermine the confidence that most consumers have in porn websites. Hmm.
Tuesday, December 04, 2007
Incident: Passport applicant finds massive privacy breach
This is interesting:
globeandmail.com: Passport applicant finds massive privacy breachA security flaw in Passport Canada's website has allowed easy access to the personal information - including social insurance numbers, dates of birth and driver's licence numbers - of people applying for new passports....
Thanks to Michael Geist for the link.
Saturday, November 24, 2007
More disks missing from HM Revenue and Customs
It's interesting what comes out when people start asking more questions: BBC NEWS Politics Six more data discs 'are missing'.
Friday, August 31, 2007
Incident: Sick Kids physician loses portable hard-drive with unencrypted personal health information
A physician from Sick Kids hospital who decided to travel with a portable hard-drive containing unencrypted health information on 3,300 patients lost the drive in Canada's busiest airport. This happened six weeks after the Information and Privacy Commissioner ordered that the hospital not allow electronic health information to leave the hospital unless it was encrypted. See: TheStar.com - living - Sick Kids doctor loses data on 3,300 patients.
Labels: air travel, airlines, health information, incident, privacy
Tuesday, August 28, 2007
Incident: Security breach hits TradeFreedom
Canadian brokerage TradeFreedom has been hit with a security breach and is notifying some of its customers that their information may have been compromised:
reportonbusiness.com: Security breach hits online brokerageOnline broker TradeFreedom Securities Inc. has quietly notified an unidentified number of its customers that a computer security breach has compromised some of their personal information, potentially exposing them to fraud.
In what it described as a follow-up to an Aug. 17 notice to clients, it said in a Friday e-mail that it had finished its investigation into the "recent unauthorized intrusion" of one of its computer systems.
"We have subsequently determined that, despite our security systems in place at the time, this unauthorized intrusion has also resulted in the compromise of some of your personal information," TradeFreedom said. "This information is your name, social insurance number, city, province and postal code."
Citing a continuing police investigation by the Sûreté du Québec, TradeFreedom president Bruce Seago said he could not release any details about the nature or timing of the computer security breach....
Friday, August 24, 2007
Incident: Monster.com criticized for waiting five days to report data breach
Wednesday, May 30, 2007
Incident: Patient information cards sold at auction in Saskatchewan
Another case of personal information being sold at auction, this time in hardcopy form:
Patient information cards sold at auctionREGINA -- The Saskatoon Health Region apologized Tuesday after more than 2,000 patient information cards that were supposed to be treated as "very confidential" were accidentally sold at an auction of health region surplus material rather than shredded.
The plastic cards are used to make imprints on documents for patient records. The cards contain names, dates of birth, addresses, religious affiliations, health card numbers and the names of the patient's doctor.
They were used between January and May of this year for day surgery patients and outpatients at City Hospital.....
Labels: health information, incident, privacy
Wednesday, May 23, 2007
Incident: Private medical records of Colorado residents exposed on Internet
MPR: wavLength: Private medical records of Colorado residents exposed on Internet Private medical records of Colorado residents exposed on Internet
Posted at 10:03 PM on May 22, 2007 by Jon Gordon
On Friday's Future Tense, you'll hear this story:
As medical records are created and transmitted electronically more and more, the chance of private information falling into the wrong hands is growing. Sometimes records are stolen by hackers, other times just improperly secured. Compromised records can lead to a range of problems, from loss of employment to identity theft to plain old embarrassment.Future Tense has discovered that detailed, personally identifiable medical records of thousands of Colorado residents were viewable on a publicly accessible Internet site for an uncertain period of time through at least last Friday, May 18. The data included patient records from at least 10 Colorado clinics and hospitals, and one hospital in Peoria, Illinois. It's unclear how many people may have seen the records.
Experts say the case likely runs afoul of federal health information privacy laws, even though there is no evidence that the records were misused.
The unsecured computer, which was accessible through a Web browser, was operated by Beacon Medical Services of Aurora, Colorado, which provides billing, coding and other services to emergency physicians at 17 facilities.
Beacon CEO Dennis Beck says he was shocked to learn about the breach and that the company took immediate steps to correct it.
"We've implemented a culture of compliance and data security and it just did not seem consistent with our culture, our practice and our experience," he said.
The medical records resided on an FTP server. FTP stands for File Transfer Protocol. It's a means by which users send and receive computer files over the Internet or private networks. In Beacon's case - and this is typical of the industry - health care providers sent encrypted data to the server for Beacon to access so it could bill patients and insurance companies. The data was unencrypted on Beacon's end, and the FTP server was not supposed to be accessible to the public. But in this case it was. No username or password was required to view the records.
The data included details of patients' visits to emergency rooms -- what ailments they complained of, diagnoses and treatments, and medical histories, along with the patients' names, occupations, addresses, phone numbers, insurance providers, and in some cases, Social Security numbers. Some of the records detailed sensitive cases, from sexually transmitted diseases to severe depression. The site also contained financial information, such as a list of low-income patients who received state aid to help pay their medical bills.
Beacon has employed two firms to help investigate what led to the security hole.
"It appears to us now at this point as if there was some back door that was opened to this server," said Beck. "We don't know when, but we believe it may have been done when a consultant did some work for us several years ago."
The company is trying to determine the exact number of patients affected, but Beck says the number looks to be fewer than 5,000.
Future Tense discovered the Beacon site after a tip from a source who stumbled upon it. We followed up on the tip, staying just long enough to confirm the existence of the records and get an idea what kind of data they contained. We notified several health care providers whose patient data was exposed. Those providers informed Beacon, which promptly shut the server down when it learned of the problem.
Bill Byron is spokesman for Banner Health Corporation, the parent company of McKee Medical Center of Loveland, Colorado, one of the providers whose data was included on the FTP site. Byron said McKee physicians won't transmit any more records to Beacon
until they're satisfied the security problem is fixed."We're trying to understand what our obligations are going to be, in terms of disclosing to patients that this has occurred, so that's still in process, to determine what we have to do," he said.
The Colorado medical records incident appears to be a serious violation of federal law governing medical record privacy, according to Janlori Goldman, director of the Health Privacy Project at Georgetown University.
"Large-scale breaches like this are not uncommon," she said. "They may not happen every day but they happen enough that you have to wonder, why aren't people taking greater care with this information?"
About a year ago, for example, a data security breach exposed medical information and Social Security numbers of some 26 million veterans after data was stolen from the home of an employee of the Department of Veterans Affairs.
Tomorrow on Future Tense, we'll explore the potential harm of compromised medical records, and at the federal law designed to protect patients. One critic of current law says patients have very little recourse when their most sensitive medical records become public.
Here is a list of physician groups, clinics and hospitals which had data of various kinds on the exposed site:
-McKee Medical Center of of Loveland, CO
-Big Thompson Emergency Physicians of Longmont, CO
-Presbyterian St. Luke's Hospital of Denver
-North Suburban Medical Center of Thornton, CO
-Carepoint Emergency Physicians of the greater Denver area
-Long's Peak Emergency Physicians
-Longmont United Hospital
-Boulder Community Hospital
-Emergency Medical Specialists PLC
-Memorial Hospital of Colorado Springs
-Proctor Hospital of Peoria, IL
Labels: health information, identity theft, incident, privacy
Sunday, May 20, 2007
Incident: Alcatel-Lucent Trying to Find Lost Disk
A courier has apparently lost a disk containing personal information on up to 200,000 employees, including dates of birth and social security numbers. In the meantime, the company will not be using couriers to transport employee information. See: Alcatel-Lucent Trying to Find Lost Disk.
Tuesday, April 24, 2007
Incident: A very personal data breach
According to BoingBoing, personal lubricant maker Astroglide has gotten itself into a slippery situation by allowing information on thousands of its customers to be accessible on the web. Information included names, addresses and lubricant purchases. Some of the information is still available through Google cache pages, showing how sticky the web can be. See: Boing Boing: Sex lube co's data breach exposes 250K+ personal records.
Tuesday, April 10, 2007
Incident: Disk with data on 2.9M Georgians lost
The beat goes on ...
Disk with data on 2.9M Georgians lost - Yahoo! NewsTue Apr 10, 12:15 PM ET
ATLANTA - A computer disk containing the names, birth dates and Social Security numbers of 2.9 million Medicaid and children's health care recipients is missing, Georgia health officials said Tuesday.
The state said the security breach was reported by Affiliated Computer Services, a private vendor with a contract to handle health care claims for the state.
The CD was lost while it was being shipped from Georgia to Maryland, ACS spokesman David Shapiro said. The company has been working with the carrier, which Shapiro would not identify, for several days to find the package, he said.
Shapiro said there was no indication anyone had tried to access any of the personal data.
"We are treating this as a missing package," he said.
Officials said the information, including addresses, covered the four-year period up to June 2006 and included some people who are no longer on the rolls.
The Georgia Department of Community Health said it was requiring the Dallas-based company to notify everyone affected and to offer free credit reports. The children's health care program involved in the data loss is called PeachCare.
PeachCare is the state's health insurance program for low-income children. Medicaid is a health insurance program for the poorest residents. Both programs are funded with a combination of state and federal dollars.
State officials notified the Centers for Medicare and Medicaid Services, the U.S. Department of Health and Human Services, the Governor's Office of Consumer Affairs and the state attorney general.
Labels: health information, incident, privacy
Saturday, February 03, 2007
Incident: Veterans Affairs hard drive with personal data missing
The Associated Press is reporting that the US Department of Veterans Affairs has lost a portable hard-drive that contained unencrypted records of thousands of veterans. See: AP Wire | 02/03/2007 | VA hard drive with personal data missing.
Saturday, January 27, 2007
Incident: Club Monaco associated with privacy breach
Fashion retailer Club Monaco is now associated with a third information breach, though the details are very sketchy. From the Globe & Mail:
globeandmail.com : globeinvestor.com : Clothing chain tipped to security breach:Fashion retailer Club Monaco has called in the RCMP to investigate a possible privacy breach involving customers' credit card numbers -- the third time in the past week that a major Canadian company has been plagued by security issues.
Club Monaco confirmed it was alerted to the problem by a credit card processor late last year and said it immediately hired a forensic firm to help the Mounties with their probe. Banks and other card issuers were also notified of the problem, and have been combing client records for any signs of fraud, according to sources in the financial community.
Investigators have found no evidence to suggest a breach occurred, a spokeswoman for the clothing chain said yesterday, adding that the data under investigation do not include names, addresses or phone numbers. She said the company has not determined how many customers might be affected.
'We've been told through the report thus far that our systems are very secure,' Wendy Smith said. 'It's an active investigation.'...
Labels: cardsystems, incident, privacy
Thursday, January 25, 2007
Winners security breach hits home
The Globe & Mail is reporting that significant fraud has been linked to the Winners information breach:
globeandmail.com: Winners security breach hits homeThousands of Canadian credit-card holders have been victimized by fraud after a security meltdown at the U.S. parent company of retail chains Winners and HomeSense, according to sources in the financial community.
They suggested that number could rise as banks and other credit-card issuers continue to gather information on what has become one of the most high-profile privacy thefts in recent memory.
“We have seen fraud on some of those accounts that we can directly link back to [the breach],” said an official with one card issuer, who cautioned his company is still determining how many of its clients could be left vulnerable by the hacking incident. He added that issuers are directly contacting any customers whose cards appear to have been used fraudulently.
Sunday, January 21, 2007
Litany of small scale privacy breaches
Last week, Global Television's main news program has aired a number of reports relating to privacy breaches at Canada Revenue Agency. This has led to a number of viewers contacting the TV network to report their own versions, involving Revenue Canada and others.
The Global Maritimes ran a report on Thursday about a woman in Nova Scotia who was repeatedly sent the credit card information, including the "secret code" for a cardholder in Ontario. When she informed them of the screw-up, they told her she was wrong and kept resending the info to her. When contacted by Global's reporter, the Ontario cardholder was furious that he had no idea that a woman in Bridgewater, Nova Scotia, could have gone to town on his Visa account and the company apparently never did anything to protect his account.
There are also a number of small scale breaches recounted as comments to the CRA breach story on the Global TV website:
Taxman moves to protect privacy
- in 1988 while living in Woodstock ON, I received an other pe... Wanda
- It happened to me last month. I received information that be... vivian
- Revenue Canada provides the Quebec Govt with income informat... Yves
- I thought maybe I should share my incident although I had ... Sherri
- This is not quite the same but equally disturbing. My husba... Margaret
- Last year I went to the post office to pick up my passport a... Elaine
- How about receiving mail from the government addressed Maureen
- Summer, 2005 I requested a Revenue Canada summary and receiv... Frank
- My dad's Disability Tax credit approval notice was enclosed ... Marnie
Labels: breach notification, incident, privacy
Saturday, January 20, 2007
Winners class action
This didn't take long: WINNERS STORES NATIONAL CLASS ACTION.
Thursday, January 18, 2007
Incidents: Rash of info breaches with Canadian connections
This has been a crazy week for privacy breaches in Canada and the week isn't over yet. I can't recall the last time I had so many media inquiries.
In addition to those below, I've been asked about two other incidents that will likely break in the next few days. (Since I heard about them from journalists, it would be rude to scoop them on the blog.)
Today we've heard of a significant announcement made by Talvest Mutual Funds
Talvest Mutual Funds issues statement regarding missing back up computer fileMONTREAL, Jan. 18 /CNW/ - Talvest Mutual Funds today announced that a backup computer file containing client information has recently gone missing while in transit between its offices.
The backup file contained information relating to the process used to open and administer approximately 470,000 current and former Talvest client accounts and may have included client names, addresses, signatures, date of birth, bank account numbers, beneficiary information and / or Social Insurance Numbers. Talvest has retained original copies of their files on its secure website.
While Talvest has no evidence to suggest this backup file has been inappropriately accessed, the manager of Talvest Mutual Funds, CIBC Asset Management, has taken precautionary measures to protect its clients. These actions include:
- Notifying all affected clients by letter.
- Compensating any affected Talvest clients for monetary loss that arises directly from unauthorized access of personal information contained on this file.
- Providing affected Talvest clients the opportunity to enrol in a credit monitoring service at no cost. This service will provide added security on client credit files at major Credit Reporting agencies.
- Establishing a dedicated call centre and website to deal with any affected Talvest client inquiries.
- Advising affected Talvest clients to regularly review activity on all their financial accounts and report any unauthorized activity immediately to their financial institution.
- Working with the police to investigate this incident and retrieve this backup file.
"We are in the process of contacting affected Talvest clients by letter to advise them of this issue and to detail the steps we are taking to safeguard their information," said Steve Geist, President of CIBC Asset Management. "Although, we have no evidence that the information contained in the backup file has been accessed in any way, we are acting out of an abundance of caution and want to assure our clients that we are taking all steps possible to address this matter. Any issue that causes disruption to our clients is of great concern to us and we regret the inconvenience this may cause our Talvest Mutual Fund Clients."
For more information on this matter, Talvest Mutual Fund clients are advised to visit www.talvest.com.
And with a report from the CBC:
CIBC loses data on 470,000 Talvest fund customersCIBC Asset Management says a backup computer file containing information on almost half a million of its Talvest Mutual Funds clients has gone missing.
The company says the missing data was in a file that disappeared "while in transit between our offices." The file had personal and financial details on current and former clients of Talvest Mutual Funds, which is a CIBC subsidiary.
The information may have included client names, addresses, signatures, dates of birth, bank account numbers, beneficiary information and/or Social Insurance Numbers.
Talvest says there's no indication that the missing backup file has been "inappropriately accessed," but says CIBC will be taking a number of precautions.
"We are in the process of contacting affected Talvest clients by letter to advise them of this issue and to detail the steps we are taking to safeguard their information," said Steve Geist, president of CIBC Asset Management.
Computer fraud expert Thomas Keenan from the University of Calgary said there's good reason for the company to alert their customers. "Because what's on there [the missing file] is everything you need to know to do identity theft," he told CBC News.
The privacy commissioner of Canada, Jennifer Stoddart, announced that she is launching an investigation.
"Although I appreciate that the bank notified us of this incident and that it is working co-operatively with my office, I am nevertheless deeply troubled, especially given the magnitude of this breach, which puts at risk the personal information of hundreds of thousands of Canadians," Stoddart said in a statement.
Talvest has set up special phone lines for clients who want more information.
The report follows news of a potential corporate privacy breach that could affect as many as two million Visa credit card holders in Canada.
The owner of Winners and HomeSense stores warned Thursday that hackers gained access to its computer system and credit card numbers may have been improperly accessed.
Also, a breach involving TJX, the parent of TJ Maxx, Winners and Homesense, may have exposed the personal information of Canadian customers of that store:
globeandmail.com: Computer breach exposes TJX shoppers to fraudSECURITY
Parent of Winners, HomeSense targeted
MARINA STRAUSS AND SINCLAIR STEWART
Tens of millions of credit card customers in Canada and the United States may have been exposed to fraud during a computer security breach at discount retailer TJX Cos., the U.S. parent of Winners and HomeSense.
TJX, which also owns T. J. Maxx and Marshalls, said yesterday it discovered the "unauthorized intrusion" in mid-December and has been working with police and security experts on both sides of the border to investigate the incident and tighten security procedures.
The retailer declined to say exactly how many customers are affected. But sources close to Visa said the company notified banks and other issuers last week that approximately 20 million of its cards around the world may have been involved. Some in the financial industry estimate the number in Canada could be as high as two million. It's not clear how many customers of other credit card companies have been left vulnerable.
The problem was tied to the computer systems that process and store information about customer transactions involving credit cards, debit cards, cheques and merchandise returns -- some of them going back to 2003. The Royal Canadian Mounted Police and the U.S. Secret Service have been called in to investigate.
"While TJX has specifically identified some customer information that has been stolen from its systems, the full extent of the theft and affected customers is not yet known," the Framingham, Mass-based retailer said in a statement.
...
"I was stunned," said retail analyst John Chamberlain at Canadian Bond Rating Service. "That's not what you expect from a big retailer. You really expect that they would have stronger systems than that. You get to the point that you trust a retailer to keep that information."
Customers consider the shopping at TJX stores as a "treasure hunt," never quite sure what they'll find, he said. As a result, customers probably use plastic there more often because they don't always know how much they'll spend, he said.
Company officials didn't return calls. Their statement said the retailer kept the matter secret until yesterday at the request of law enforcement. The company said it promptly notified credit card companies and firms that process customer transactions.
An intruder grabbed information dealing with credit and debit cards sales in TJX stores during 2003 and part of 2006, according to the company. However, a source said that the debit transactions were confined to the U.S. market. TJX has been able to identify "a limited number" of credit card and debit card holders whose information was taken.
Canadian banks are scrambling to assess the potential damage. Tania Freedman, a Visa spokeswoman, said the company is forwarding information to banks. "These accounts were potentially exposed, [but] not all accounts that are exposed will experience fraud," she said, adding that customers are protected by the card's zero-liability policy.
...
In Canada, TJX runs 184 Winners and 68 HomeSense stores.
Expect much more info to come.....
Update (20070118): The Privacy Commissioner of Canada has inititated a complaint on her own accord related to the Talvest breach: Privacy Commissioner launches investigation of CIBC breach of Talvest customers' personal information.
Labels: cardsystems, identity theft, incident, privacy, retail, tjx
Thursday, January 04, 2007
Incident: CRA misdirects taxpayer information
A Halifax resident was more than slightly surprised when he went to the Canada Revenue Agency to pick up his requested notice of assessment. While the notice was conspicuously absent from the envelope, he did find a raft of information about ten complete strangers. Apparently, the CRA stuffed the wrong envelopes and handed over confidential and sensitive information to the wrong person.
When the individual who received the information was not satisfied with the CRA's reaction, he called the other taxpayers and went to the media. The story is on the front page of the Halifax Chronicle Herald.
To make matters worse, the notice of assessment was mailed but nobody knows who to.
CTV is doing a piece for the supper hour news here in Halifax, for which I was interviewed earlier today. They are hoping to get some comment from the unshuffled Minister responsible for CRA.
From today's paper:
More than he wanted to knowGovernment mistakenly mails other people’s tax papers to Whites Lake man
By JOHN GILLIS Staff Reporter
Andrew Doiron of Whites Lake just wanted to find out his RRSP contribution limit for the year. But what he got was a raft of personal information about 10 strangers from as far away as British Columbia.
The Canada Revenue Agency is now investigating how the confidential tax documents landed in Mr. Doiron’s mailbox and where the information he requested ended up.
"It looks like somebody just picked a handful of paper off a printer and just slipped it in an envelope with my (address) page on top," Mr. Doiron said Wednesday. "But of course they didn’t put my papers in there."
The confusion began Dec. 20 when Mr. Doiron went to the Canada Revenue Agency’s Halifax office in person to ask for a copy of his notice of assessment. He was told he had to call a toll-free number to ask for the document. Staff let him use a phone in the building.
Mr. Doiron was surprised Tuesday when he found an envelope from the agency in his mailbox, and it contained about 35 pages. The documents bore the names, addresses, social insurance numbers, income, marital status and other personal information for 10 other people. His own notice of assessment was not included.
He immediately called a toll-free Canada Revenue Agency number again but said it was tough to persuade the person who answered to let him speak to a supervisor. When he finally did, he said he was asked to mail the documents back to the agency and advised he could claim the price of the postage stamp on his tax return next year.
Mr. Doiron also called as many of the people whose tax information he’d been sent as possible.
One, Sandra Ambersley of Brampton, Ont., told CTV she was very concerned about what might have happened if someone had wanted to use that information.
"I was totally shocked yesterday when I received a call from Halifax, this man saying that he’d received all my personal information," she said Wednesday.
Mr. Doiron noted that on the same online telephone directory he used to find people’s telephone numbers, there was an ad pointing to a Capital One credit card application that required only an address and a social insurance number.
He personally returned all the strangers’ documents to the Halifax office Wednesday.
Mr. Doiron said he felt he did not get a serious response from the agency until after he began contacting the media.
Jack Lee, acting director of the Nova Scotia office, called to apologize and had a copy of the notice of assessment Mr. Doiron requested sent to him. It arrived safely.
The notice had been mailed previously, but not to him.
"Mine’s out there somewhere, floating around," Mr. Doiron said. "I hope somebody threw it away."
Canada Revenue Agency spokesman Roy Jamieson said security is the No. 1 priority for the service, but mistakes happen.
"We’re certainly scrambling to try and piece together what took place," he said. "There’s quite an active and quite an intense investigation going on right now."
He said a call to a toll-free number could be answered at any one of a number of call centres across the country, depending in part on the nature of the request. A requested document could be printed at the appropriate location and mailed from there.
The agency sends about 90 million pieces of mail per year and it’s rare that something gets mixed up, he said.
"To be misdirected in the magnitude of this case, it’s certainly unusual," Mr. Jamieson said.
He said the agency will contact all of the people whose documents were involved and will keep Mr. Doiron abreast of its investigation into the mix-up.
"There’s no question that any kind of breach of security and compromising of an individual’s privacy and confidentiality is our most significant issue in this agency," Mr. Jamieson said.
Mr. Doiron has little confidence that anything will change.
"My gut feeling is, this is government, nothing’s going to happen," he said.
Update: From CTV:
Canada Revenue investigates botched mailoutThe Canada Revenue Agency is scrambling to restore public trust and has launched an internal investigation after confidential information on several Canadians was sent to a Halifax-area man.
Documents that Andy Doiron of White's Lake, N.S., were mistakenly sent include social insurance numbers, income, addresses and the marital status of 10 Canadians, including some from as far west as Edmonton.
Doiron said he called most of the people to tell them what happened, and returned the documents to Revenue Canada.
With the trust of Canadians potentially on the line and tax time just around the corner, the agency is promising tough action if necessary.
Revenue Canada spokesperson Roy Jamieson called the incident a rare case of misdirected mail, but admitted somebody in the department made a mistake.
"Certainly if we identify breaches of policy process and procedure, there are disciplinary measures that can be taken and I expect they will be looked at quite seriously," he told CTV Atlantic.
Federal Minister of National Revenue Carol Skelton said she was "disturbed" by the security breach.
"The instant that I found out about it we had launched an investigation," she told CTV News in Saskatoon. "I really can't say much more about it than that. The incident is being looked into."
The agency is still trying to determine which one of five locations was responsible for the botched mail out.
David Fraser, a legal expert in security matters, told CTV Halifax that if such information were to fall in the wrong hands, it could easily be used to commit fraud.
"There really does need to be something done in order to make sure the trust is always there. Accidents happen but so often trust is won or lost in the aftermath of how they decide to deal with it," he said.
Sandra Ambersley of Brampton, Ont. was one of the people Dorion called.
"I was totally shocked when I received the call (on Tuesday) from Halifax," Ambersley told CTV Toronto.
"This man (was) telling me that he received all my personal information. As a joke he did say 'I could duplicate you right now.'"
The confusion began when Doiron called the revenue agency on Dec. 20 requesting a copy of his notice of assessment.
On Tuesday, an envelope from the agency arrived in his mailbox, containing over 30 pages of documents with all the information. His own assessment wasn't included.
Doiron said he immediately called the toll-free Canada Revenue Agency number again and he was asked to mail the documents immediately.
With a report from CTV Atlantic reporter Marc Patrone.
Labels: bc, incident, media-mention, privacy, privacy act, public sector, vanity
Friday, December 29, 2006
Incident: Pharmacy customers' personal information found in Winnipeg alley
A Winnipegger found three shopping bags' worth of prescription documents in an alley behind hospital this week. First stop? The media, of course.
Labels: health information, incident, manitoba, privacy
Wednesday, December 20, 2006
Canada Revenue Agency investigates leaks of info on high profile taxpayers
The Canada Revenue Agency generally takes taxpayer privacy very seriously. It's rare to hear about any leak or misuse of personal information from the federal tax department. Lately, however, the CRA, or at least some of its employees, have come under suspicion as confidential records of high-profile taxpayers have appeared online.
The Candian Press reports on a leak of information about MP and former hockey star Ken Dryden:
Tax office staff warned of disciplinary action as CRA probes Dryden tax leakGREGORY BONNELL
TORONTO (CP) - Canada Revenue Agency workers are being warned of disciplinary action, including dismissal, following a published report that federal employees had leaked the confidential tax information of Liberal MP Ken Dryden.
"It is unsettling to consider that not all employees may be working with the degree of professionalism and integrity that the CRA expects," writes Larry Hillier, assistant commissioner for the Ontario region, in an internal e-mail to CRA employees obtained by The Canadian Press.
"As with all allegations of wrongdoing, an immediate investigation is being launched to determine if a breach of our standards has occurred," the memo reads. "If warranted, disciplinary action will be taken, up to and including termination of employment."
The tax information of Dryden and several other sports personalities, including former Toronto Maple Leaf Borje Salming, is available on the Internet courtesy of debt collectors who have been illegally leaking the information.
National Revenue Minister Carol Skelton has asked the CRA to launch an immediate investigation in the wake of the original CP report, which was published Saturday.
CRA workers are violating the Income Tax Act, the Privacy Act, and possibly criminal law by feeding information to former employee Alan Baggett, who in turn posts the disclosures to an Internet chat group.
The Dryden story, posted in May 2005, says the former Montreal Canadiens goalie and Leafs general manager once had a "small personal tax debt, which he no doubt paid." A former employee who worked on Dryden's file confirmed the debt to CP.
Neither Dryden nor Salming replied to requests for comment on the postings. The postings did not indicate Dryden's current tax situation.
CRA employees who are found guilty of disclosing tax information, a violation of the Income Tax Act, face fines of up to $5,000 or jail time of up to 12 months - a fact Hillier points out in his memo.
"When one employee breaches confidentiality, as is currently alleged, each and every one of us is impacted," Hillier writes, noting his "high level of confidence in the employees of the Ontario Region."
"You can be assured that all necessary steps are being taken to thoroughly investigate this matter."
Depending on the circumstances, the disclosure of confidential information could also constitute a criminal offence. Under the Criminal Code of Canada, breach of trust by a public officer is punishable by a maximum prison sentence of five years.
Labels: cra, incident, privacy, public sector
Tuesday, December 12, 2006
Incident: UCLA database with 800K SSNs hacked
I stopped reporting on information breaches some time ago as they have become too routine. But this one bears commenting upon:
It appears that a database at UCLA containing over eight hundred thousand social security numbers has been hacked. Repeatedly. For over a year. What is most remarkable about this is that a large portion the affected individuals have never been students or employees of the university. Many simply applied for admission, in some cases years before.
Repeat after me: Only collect the information you need (actually, really need) and then only keep it for as long as you actually, really need it.
Personal information is like an underground oil tank. If you need one, they're good to have. Heck, if you need two, have two. But oil tanks are inherently risky. If you don't need an oil tank, for goodness' sake don't put one on your property. If you no longer need it, get rid of it. If you just leave it on your property, the risks leaks (and the ensuing cleanup cost) is too high. It doesn't matter if oil tanks and personal information appear free.
See: Boing Boing: Major identity leak: UCLA database with 800K SSNs hacked
Wednesday, December 06, 2006
Calgary Health Region found in Contravention of Health Information Act over stolen laptop
The Office of the Information and Privacy Commissioner of Alberta has found that the Calgary Health Region violated the Health Information Act in connection with a stolen laptop:
Calgary Health Region found in Contravention of Health Information Act over stolen laptop:The Office of the Information and Privacy Commissioner has found that the Calgary Health Region contravened the Health Information Act (HIA), following an investigation into the theft of a laptop computer. The laptop contained a database of more than 1,000 children in a mental health care program, including patient history and treatment details.
Key findings included:
- The Health Region had policies in place that would have protected the stolen laptop and the information it contained, but those policies were not fully implemented by the Collaborative Mental Health Program.
- A copy of the entire database was stored on the stolen computer, increasing the number of people affected. Program workers should only have copied the files they needed, rather than the entire database.
- While the laptop was protected by passwords, this was not adequate given the nature of the information it contained
- A knowledgeable and motivated individual could access the data with tools that are readily available on the internet.
- While the risk of identity theft from the information is low, it cannot be ruled out.
- Encryption technology would have protected the lost data, but it was not implemented.
The CHR informed the Commissioner's Office of the incident on its own initiative, took immediate action to notify affected individuals and has since implemented measures to secure mobile computers. The Health Region also agreed to follow our Investigator's recommendations.
Investigator Brian Hamilton says, "For the most part the Calgary Health Region does a good job protecting information, and has been taking steps to improve security. Unfortunately, they failed to recognize and address the risks of mobile computing in this program area."
Others can learn from this investigation. The Office of the Information and Privacy Commissioner urges all HIA custodians, public bodies and private sector organizations to follow these recommendations for mobile computing:
- Perform a Privacy Impact Assessment (or a security risk assessment) before implementing mobile computing.
- Do not store personal or health information on mobile computing devices unless you need to - consider technologies that allow secure, remote access to your network and data instead.
- If you must store personal or health information on a mobile device, use encryption to protect the data - password protection alone is not sufficient.
- Keep the amount of personal or health information stored on mobile computing devices to a minimum, based on your business needs.
- Periodically check your policies against practice to ensure they reflect reality and remain effective.
- Provide specific training on mobile computing to staff to ensure they understand the risks and understand how to protect their equipment.
-30-
For more information or to view a copy of Investigation Report H2006-IR-002, visit our website, http://www.oipc.ab.ca/.
Labels: alberta, health information, identity theft, incident, laptop, privacy
Thursday, November 23, 2006
Charges laid under Alberta's Health Information Act
The Information and Privacy Commissioner of Alberta has announced that the first charges ever have been laid under the Helath Information Act. The charges relate to improper access to health information and misleading the OIPC's investigator. From the OIPC's media release:
Charges laid under Health Information Act:November 23, 2006
Four charges have been laid against an individual under the Health Information Act. She has been summoned to appear in Calgary Court on January 15, 2007. This is the first time charges have been laid under provisions of the Health Information Act.
As a result of a complaint to the Office of the Information and Privacy Commissioner an investigation was undertaken. Upon completion of the investigation, the matter was referred to the Regulatory Prosecutions Office of Alberta Justice. Following that consultation, two charges were laid for improperly accessing another individual's health information and two charges were laid for misleading the Office of the Information and Privacy Commissioner's investigator.
The maximum penalty for a first offence under the Health Information Act is $50,000 for each charge.
Alberta's Information and Privacy Commissioner, Frank Work, says, 'These are serious allegations, and they are not to be taken lightly. As we move increasingly to electronic health records, the security of Albertan's health information remains paramount. We will do everything in our power to help protect this information'.
Labels: alberta, health information, incident, privacy
Thursday, October 12, 2006
Incident: Hacker steals personal information from Brock University computers
I have generally stopped reporting privacy and security incidents, since the sheer numbers are overwhelming. But I'll make an exception for this one, since it involves a Canadian university...
Hackers steal personal information from Brock University computers:The personal information — including some credit card and bank account numbers — of about 70,000 people who gave money to Brock University has been stolen from the school's computers by a hacker.
Terry Boak, Brock's vice-president academic, said the digital intruder had the secret passwords needed to access the file listing of possibly every individual to ever donate to the university.
'It wasn't just someone who hacked in by playing around with it,' Boak said. 'So, you start thinking about how these passwords were obtained.'
Boak said the hacker tapped into the system on Sept. 22 at 5:27 p.m. ET, taking only four minutes to make off with the file containing thousands of names, birthdates and e-mail addresses.
About 90 credit card numbers and some 270 bank account details were also in the file.
Boak said those people were called within 24 hours, while the remaining thousands received a letter in the mail explaining what had happened.The personal information — including some credit card and bank account numbers — of about 70,000 people who gave money to Brock University has been stolen from the school's computers by a hacker.
Terry Boak, Brock's vice-president academic, said the digital intruder had the secret passwords needed to access the file listing of possibly every individual to ever donate to the university.
'It wasn't just someone who hacked in by playing around with it,' Boak said. 'So, you start thinking about how these passwords were obtained.'
Boak said the hacker tapped into the system on Sept. 22 at 5:27 p.m. ET, taking only four minutes to make off with the file containing thousands of names, birthdates and e-mail addresses.
About 90 credit card numbers and some 270 bank account details were also in the file.
Boak said those people were called within 24 hours, while the remaining thousands received a letter in the mail explaining what had happened.
Thursday, September 14, 2006
Incident: BC Government and service provider lose 33 data tapes with info on hundreds of thousands
A while ago, the BC government caught auctioning off backup dapes containing loads of pesonal information (The Canadian Privacy Law Blog: Incident: British Columbia government actioned off surplus backup tapes with sensitive health information). Now, IT Business has discovered that 33 backup tapes sent missing from a British Columbia government data centre. An investigation turned of three of the tapes, but the rest remain AWOL. Some of the tapes contain very sensitive personal information about welfare recipients and others contain even more sensitive health information.
What's worse is that the tapes were lost in August of last year and the investigation was completed in February, but it took a Freedom of Information Act request for the information to come to light.
See: ITBusiness - B.C. loses track of computer tapes with citizens' data: Information about income assistance, prescriptions and identifying details of hundreds of thousands of people goes missing. Telus comments on its role and its efforts to lock down the data centre
Labels: bc, british columbia, health information, incident, privacy
Tuesday, August 29, 2006
Incident: AT&T e-commerce site hacked
AT&T is again in the privacy crosshairs, this time after it was revealed that credit card info of around 19,000 customers was obtained by "hackers" via an e-commerce website operated by the telco. See: AT&T: Hackers Took Credit Card Info - Forbes.com.
Friday, July 14, 2006
Incident: Privacy breach hits +200K online game players
From GameSpot (via the always interesting Video Game Law Blog):
Japanese MMOG suffers privacy leak - News at GameSpotGame Garden warns that e-mail addresses and game logs of hundreds of thousands of Xenepic Online players may have been compromised.
By Walt Wyman, GameSpot
Posted Jun 28, 2006 11:41 am PT
Game Garden, an online game developer and provider, announced today that personal user information from Xenepic Online, a free massively multiplayer online role-playing game for PCs, was inadvertently compromised. Game Garden manages the server on behalf of NHN Japan Corporation, the game's provider.
The information was mistakenly stored on an open download server, potentially allowing anyone to access it using certain exploits. Data for 297,805 users was put at risk, including their game-server usernames and passwords, e-mail addresses, and game log files, which contain information on items purchased and chat history.
However, it seems that no payment information, such as credit card information, was among the compromised data. In a press release, Game Garden apologized to Xenepic users for the security failure and pledged to "further consolidate internal management to prevent similar incidents in the future."
Labels: incident, ip address, privacy, retention
Sunday, July 02, 2006
Incident: Laptops stolen from American Red Cross office in Texas
According to the Dallas Morning News, three laptops were stolen from a locked closet in a Texas office of the American Red Cross. The laptops contained years of data on all donors from that particular region, but all the data was encrypted. Because it was encrypted, it should probably classified as a "non-incident" or "incident averted".
See: Dallas Morning News | Donor data stolen at local Red Cross .
Saturday, June 24, 2006
Incident: Personal info on thousands of US sailors found on website
Info on thousands of US Navy sailors somehow found their way onto a website, including names, addresses and social security numbers:
Navy Finds Data on Thousands of Sailors on Web SiteNavy officials discovered this week that personal information on nearly 28,000 sailors and family members was compromised when it appeared on a Web site, fueling more concerns about the security of sensitive information belonging to federal employees.
Five spreadsheet files of data -- including names, birth dates and Social Security numbers of sailors and their relatives -- were found exposed on a Web site Thursday night during routine internal sweeps of the Internet for sensitive material, said Lt. Justin Cole, a spokesman for the chief of naval personnel. He said the material was removed from the Web site within two hours....
Meanwhile, the Canadian navy has lost a torpedo.
Incident: FTC laptops stolen, along with personal data
The American Federal Trade Commission is usually at the forefront of slapping around companies who do not take adequate steps to secure personal information. So it is a bit ironic that two FTC laptops have been stolen from a locked car, along with personal information on around one hundred defendants in current FTC investigations. Check it out: FTC laptops stolen, along with personal data.
Thursday, June 22, 2006
Incident: Laptop stolen with Equifax employee info
The Privacy Law Site is reporting that an employee of Equifax had his laptop stolen in Europ last month. The computer contained names and social security numbers for all of the company's US-based employees. See: The Privacy Law Site: Equifax Laptop Stolen.
Why would an employee need to travel with that information? I dunno.
See also: Chron.com | Equifax: Laptop With Employee Data Stolen.
Labels: incident, laptop, privacy, public sector, workplace
Wednesday, June 21, 2006
Incident: Visa says February ATM breach may have exposed data
Apparently, Visa has come clean (sort of) about a large debit-card breach from earlier this year:
Visa says ATM breach may have exposed data - Yahoo! NewsSAN FRANCISCO - Visa USA on Tuesday confirmed an ATM security breakdown has exposed more consumers to potential mischief, the latest in a long line of lapses that have illuminated the often flimsy controls over the personal information entrusted to businesses, schools and government agencies.
The latest breach dates back to February when San Francisco-based Visa began notifying banks of a security problem affecting a U.S.-based contractor that processed automated teller machine transactions. Visa, one of the nation's largest issuer credit and debit cards, publicly acknowledged the trouble Tuesday in response to media inquiries prompted by Wachovia Bank's decision to replace an untold number of debit cards issued to its customers.
Charlotte, N.C.-based Wachovia issued the card replacements last week as an antifraud measure, said bank spokeswoman Mary Beth Navarro. She declined to explain the circumstances that triggered the action after several months. Visa also gave out few details about the incident. Thousands of banks have issued millions of debit cards bearing the Visa logo.
In a statement, Visa said it is working with its member banks and authorities "to do whatever is necessary to protect cardholders."...
Sunday, June 18, 2006
Incident: Laptop with D.C. workers' data stolen
There goes another one: Laptop with D.C. workers' data stolen - Yahoo! News.
Labels: incident, information breaches, laptop, privacy
Friday, June 16, 2006
Incident: Porn-surfing employee compromises personal information on 2,300 Oregon taxpayers
Incident: Computerworld is reporting that an employee of the Oregon Department of Revenue downloaded trojan software along with porn videos, apparently compromising personal information about 2,300 Oregon taxpayers: Trojan horse captured data on 2,300 Oregon taxpayers from infected gov't PC.
Lesson: Practice safe surfing or you might get infected.
Labels: incident, information breaches, privacy, public sector, workplace
Tuesday, June 13, 2006
Incident: Massive personal information leak at Japanese telco
Japan's second largest mobile phone operator has reported that personal information on almost four million subscribers has been compromised. Two arrests have been made in the breach, which was apparently an inside job and an attempt to blackmail the company.
KDDI reports massive personal data leak - Yahoo! NewsTue Jun 13, 7:53 AM ET
TOKYO (AFP) - KDDI Corp, Japan's number two mobile operator, said that private information on nearly four million subscribers to its Internet service had been leaked.
Police said extortionists tried to sell the data which included the names, addresses, contact numbers, sex, birthdate and e-mail addresses of those who applied for KDDI's Dion Internet service by December 18, 2003.
But information such as their passwords, bank account information and communications logs has not released, the company said.
Tadashi Onodera, KDDI president and chairman, offered a public apology at a press conference.
'We consider that this will hurt our company's credibility. We will do our best to restore customers' trust by explaining the issue,' Onodera told reporters, although he said there were no plans for compensation.
Information seems to have been leaked by KDDI employees or a vendor who had access to the system because it is impossible to access it from the outside, Onodera said.
Police said they arrested two men who attempted extortion in the case, reportedly demanding KDDI pay five million to 10 million yen (43,700 to 87,000 dollars) for the data.
Onodera declined to comment on the issue as it is under police investigation.
KDDI learned about the leak through an anonymous phone call on May 30 and the next day a person handed a CD-ROM with data from 400,000 customers to its headquarters' reception desk, he said.
Labels: incident, information breaches, privacy
Incident: Files Of 150,000 Voters Missing
Whatever you do, don't let that 500 pound cabinet out of your sight.
Apparently a half-ton filing cabinet containing records of 150,000 voters in Colorado has "gone missing". It didn't walk away, but might have been misplaced when the Denver Election Commission moved offices. So if you see a lonely, lost filing cabinet, give them a call.
All Headline News - Files Of 150,000 Voters Missing - June 13, 2006:Files Of 150,000 Voters Missing
June 11, 2006 8:38 a.m. EST
Mary K. Brunskill - All Headline News Contributor
Denver, Colorado (AHN) - Police were notified Saturday that records containing personal information on over 150,000 voters are missing at Denver election offices, and officials are investigating to find whether the files were lost, moved or stolen.
A 500-pound cabinet containing microfilmed voter registration files from 1989 to 1998, which contained voters' Social Security numbers, addresses and other personal information, disappeared in February when the commission moved to new offices.
Officials were not aware the records were missing until June 1 and the Denver Election Commission is trying to determine why officials did not learn the files were missing earlier, the AP reports.
Commission spokesman Alton Dillard told the Rocky Mountain News in Saturday's edition, 'We will get to the bottom of it.'
Dillard said staffers are searching the commission's new and old offices and its warehouse and employees of the moving company are being questioned.
Thanks to a correspondent from Vancouver, who led me to Interesting People, which linked to Hard To Do Any Worse, which in turn persuaded me to click on All Headline News.
Labels: incident, information breaches, privacy
Friday, June 09, 2006
Incident: Security clearance info on nuclear contractors compromised by hacker
Not a good couple of weeks for information security in the US Government. It is now being reported that a hacker penetrated a computer system of the Department of Energy's Nuclear Weapons Agency in September, but the Secretary of Energy was not informed until last week. Here's a bit more info:
DOE computers hacked; info on 1,500 taken - Yahoo! News:Although the compromised data file was in the NNSA's unclassified computer system -- and not part of a more secure classified network that contains nuclear weapons data -- the DOE officials would provide only scant information about the incident during the public hearing.
Brooks said the file contained names, Social Security numbers, date-of-birth information, a code where the employees worked and codes showing their security clearances. A majority of the individuals worked for contractors and the list was compiled as part of their security clearance processing, he said.
Tom Pyke, DOE's official charged with cyber security, said he learned of the incident only a few days ago. He said the hacker, who obtained the data file, penetrated a number of security safeguards in obtaining access to the system.
Labels: incident, information breaches
Thursday, June 08, 2006
Incident: IRS employee loses laptop with personal info on 291 employees and job applicants
From the Washington Post:
IRS Laptop Lost With Data on 291 People:The IRS's Terry L. Lemons said the employee checked the laptop as luggage aboard a commercial flight while traveling to a job fair and never saw it again. The computer contained unencrypted names, birth dates, Social Security numbers and fingerprints of the employees and applicants, Lemons said. Slightly more than 100 of the people affected were IRS employees, he said. No tax return information was in the laptop, he said.
'The data was not encrypted, but it was protected by a double-password system,' Lemons said. 'To get in to this personal data on there, you would have to have two separate passwords.'...
Labels: incident, information breaches, laptop
Wednesday, June 07, 2006
Incident: Info on 300K+ CPAs goes missing along with hard-drive
If you don't need (really, really need) a particular type of personal information and it is at all sensitive, do not collect it. Do not keep it. If you have it, securely destroy it.
Privacy best practices world wide are pretty clear that you should only collect and retain personal information that is necessary for a clearly articulated purpose. In the CSA Model Code for the Protection of Personal Information, it is articulated thusly:
4.4 Principle 4 - Limiting CollectionThe collection of personal information shall be limited to that which is necessary for the purposes identified by the organization. Information shall be collected by fair and lawful means.
This goes hand-in-hand with the principle that you should only keep information for as long as is reasonably necessary to fulfil those clearly articulated purposes. Take it away, CSA Code:
4.5 Principle 5 - Limiting Use, Disclosure, and RetentionPersonal information shall not be used or disclosed for purposes other than those for which it was collected, except with the consent of the individual or as required by law. Personal information shall be retained only as long as necessary for the fulfilment of those purposes.
Generally Accepted Privacy Principles produced by the Canadian Institute of Chartered Accountants in Canada and the American Institute of Certified Public Accountants include variations on these general rules:
4. Collection. The entity collects personal information only for the purposes identified in the notice.5. Use and Retention. The entity limits the use of personal information to the purposes identified in the notice and for which the individual has provided implicit or explicit consent. The entity retains personal information for only as long as necessary to fulfill the stated purposes.
So I guess you can draw from these examples that you should not collect or keep someone's social security number or social insurance number unless you really need it.
Interestingly and ironically, this lesson has just been learned the hard way by the American Insitute of Certified Public Accountants. The AICPA has just reached the conclusion that it should apply at least a portion of its own Generally Accepted Privacy Principles with respect to the personal information about its members that it collects and retains. It appears that a hard-drive containing personal information on 330,000 members, including social security numbers, has gone missing while in the custody of an overnight courier. While it is very easy to blame the courier, it is clear that the AICPA has no compelling reason to collect SSNs. In fact, there's no reason that even roughly corresponds to the risk associated with keeping such data around, let alone couriering it to a service provider.
To read more, check out: CPA group says hard drive with data on 330,000 members missing.
Labels: incident, information breaches, retention
Sunday, June 04, 2006
Incident: Hotels.com customer info on laptop stolen from auditor in February
OK. Now I'm a little mad. Another laptop reportedly stolen from an auditor. These have gotten too routine.
But this time, there's a good chance my personal information may have been on the stolen laptop. The data is from Hotels.com, a subsidiary of Expedia.com. This company also handles hotels booked through the Air Canada website using their Destina service. This is a service I've used in the past.
I haven't gotten a letter, but with information on 243,000 customers, I expect this is a subset of customers from 2002, 2003, 2004.
It is particularly rich that Hotels.com and Ernst & Young is suggesting that customers "take appropriate action to protect their personal information". Hello? You're suggesting that I take appropriate action to protect my personal information? How about you and your auditors taking appropriate action to protect my personal information. You can start by not letting it leave the building on a laptop. But if you don't follow that basic step, you could think about encrypting the information.
Here's the story from the Associated Press:
Hotels.com customer info may be at risk - Yahoo! News:SEATTLE - Thousands of Hotels.com customers may be at risk for credit card fraud after a laptop computer containing their personal information was stolen from an auditor, a company spokesman said Saturday.
The password-protected laptop belonging to an Ernst & Young auditor was taken in late February from a locked car, said Paul Kranhold, spokesman for Hotels.com, a subsidiary of Expedia.com based in Bellevue, Wash.
"As a result of our ongoing communication with law enforcement, we don't have any indication that any credit card numbers have been used for fraudulent activity," Kranhold said. "It appears the laptop was not the target of the break-in."
Both Hotels.com and Ernst & Young mailed letters to Hotels.com customers this past week encouraging them to take appropriate action to protect their personal information.
The transactions recorded on the laptop were mostly from 2004, although some were from 2003 or 2002, the companies said. The computer contained personal information including names, addresses and credit card information of about 243,000 Hotels.com customers. It did not include their Social Security numbers.
Ernst & Young, which has been the outside auditor for Hotels.com for several years, notified the company of the security breach on May 3.
"We deeply regret this incident has occurred and want to apologize to you and Hotels.com for any inconvenience or concern this may cause," said the unsigned memo from Ernst & Young dated May 2006.
Ernst & Young invites those affected by the incident to enroll in a free credit monitoring service arranged by the auditor.
"We sincerely regret that this incident occurred and we are taking it very seriously," said the letter signed by Hotels.com general manager Sean Kell.
The letter from Hotels.com said "Ernst & Young was taking additional steps to protect the confidentiality of its data, including encrypting the sensitive information we provide to them as part of the audit process."
Labels: incident, information breaches, laptop
Sunday, May 28, 2006
Incident: Sacred Heart computer security breach affects 135,000
Security breaches at universities are such old news that I've stopped reporting them on this blog. But this one is a bit different. A computer security breach has resulted in the compromise of personal information of 135,000 people at Sacred Heart University in Connecticut. (Yawn.) But what's notable is that many of those affected are not alumni, not staff, not students, not applicants. The university had obtained information on prospective students from dozens of sources, likely without the OK of those individuals. And some of this information was compromised in the breach. Yup. That's a new one. And not a good one.
See: Wtnh.com, Connecticut News and Weather - Sacred Heart computer security breach affects 135,000.
Labels: incident, information breaches
Monday, May 22, 2006
Incident: Personal information about 26.5M US veterans on laptop stolen
An employee of the United States Department of Veterans' Affairs took home a laptop containing data on 26.5 million American veterans, which was subsequently stolen from his home. Authorities do not think the information has been misused:
Personal Data of 26.5M Veterans Stolen - Yahoo! NewsWASHINGTON - Personal data, including Social Security numbers of 26.5 million U.S. veterans, was stolen from a Veterans Affairs employee this month after he took the information home without authorization, the department said Monday.
Veterans Affairs Secretary Jim Nicholson said there was no evidence so far that the burglars who struck the employee's home have used the personal data — or even know they have it. The employee, a data analyst whom Nicholson would not identify, has been placed on leave pending a review.
"We have a full-scale investigation," said Nicholson, who said the FBI, local law enforcement and the VA inspector general were investigating. "I want to emphasize, there was no medical records of any veteran and no financial information of any veteran that's been compromised."
"We have decided that we must exercise an abundance of caution and make sure our veterans are aware of this incident," he said in a conference call with reporters.
The theft of veterans' names, Social Security numbers and dates of birth comes as the department has come under criticism for shoddy accounting practices and for falling short on the needs of veterans.
Last year, more than 260,000 veterans could not sign up for services because of cost-cutting. Audits also have shown the agency used misleading accounting methods and lacked documentation to prove its claimed savings.
Veterans advocates immediately expressed alarm....
The federal government has put up an information page here:
Latest Information on Veterans Affairs Data Security -- Firstgov.govLatest Information on Veterans Affairs Data Security
The Department of Veterans Affairs (VA) has recently learned that an employee, a data analyst, took home electronic data from the VA, which he was not authorized to do. This behavior was in violation of VA policies. This data contained identifying information including names, social security numbers, and dates of birth for up to 26.5 million veterans and some spouses, as well as some disability ratings. Importantly, the affected data did not include any of VA's electronic health records nor any financial information. The employee's home was burglarized and this data was stolen. The employee has been placed on administrative leave pending the outcome of an investigation.
Appropriate law enforcement agencies, including the FBI and the VA Inspector General's office, have launched full-scale investigations into this matter. Authorities believe it is unlikely the perpetrators targeted the items because of any knowledge of the data contents. It is possible that they remain unaware of the information which they possess or of how to make use of it. However, out of an abundance of caution, the VA is taking all possible steps to protect and inform our veterans.
The VA is working with members of Congress, the news media, veterans service organizations, and other government agencies to help ensure that veterans and their families are aware of the situation and of the steps they may take to protect themselves from misuse of their personal information. The VA will send out individual notification letters to veterans to every extent possible. Additionally, working with other government agencies, the VA has set up a manned call center that veterans may call to get information about this situation and learn more about consumer identity protections. That toll free number is 1-800-FED INFO (1-800-333-4636). The call center will operate from 8 am to 9 pm (EDT), Monday-Saturday as long as it is needed.
Here are some questions you may have about this incident, and their answers.
I'm a veteran. How can I tell if my information was compromised?
At this point there is no evidence that any missing data has been used illegally. However, the Department of Veterans Affairs is asking all veterans to be extra vigilant and to carefully monitor bank statements, credit card statements and any statements relating to recent financial transactions. If you notice unusual or suspicious activity, you should report it immediately to the financial institution involved and contact the Federal Trade Commission for further guidance.
What is the earliest date at which suspicious activity might have occurred due to this data breach?
The information was stolen from an employee of the Department of Veterans Affairs during the month of May 2006. If the data has been misused or otherwise used to commit fraud or identity theft crimes, it is likely that veterans may notice suspicious activity during the month of May.
I haven't noticed any suspicious activity in my financial statements, but what can I do to protect myself and prevent being victimized by credit card fraud or identity theft?
The Department of Veterans Affairs strongly recommends that veterans closely monitor their financial statements and review the guidelines provided on this webpage or call 1-800-FED-INFO (1-800-333-4636).
Should I reach out to my financial institutions or will the Department of Veterans Affairs do this for me?
The Department of Veterans Affairs does not believe that it is necessary to contact financial institutions or cancel credit cards and bank accounts, unless you detect suspicious activity.
Where should I report suspicious or unusual activity?
The Federal Trade Commission recommends the following four steps if you detect suspicious activity:
- Step 1 – Contact the fraud department of one of the three major credit bureaus:
Equifax: 1-800-525-6285; http://www.firstgov.gov/external/external.jsp?url=http://www.equifax.com; P.O. Box 740241, Atlanta, GA 30374-0241
Experian: 1-888-EXPERIAN (397-3742); http://www.firstgov.gov/external/external.jsp?url=http://www.experian.com; P.O. Box 9532, Allen, Texas 75013
TransUnion: 1-800-680-7289; http://www.firstgov.gov/external/external.jsp?url=http://www.transunion.com; Fraud Victim Assistance Division, P.O. Box 6790, Fullerton, CA 92834-6790
- Step 2 – Close any accounts that have been tampered with or opened fraudulently.
- Step 3 – File a police report with your local police or the police in the community where the identity theft took place.
- Step 4 – File a complaint with the Federal Trade Commission by using the FTC's Identity Theft Hotline by telephone: 1-877-438-4338, online at http://www.firstgov.gov/external/external.jsp?url=http://www.consumer.gov/idtheft, or by mail at Identity Theft Clearinghouse, Federal Trade Commission, 600 Pennsylvania Avenue NW, Washington DC 20580.
I know the Department of Veterans Affairs maintains my health records electronically; was this information also compromised?
No electronic medical records were compromised. The data lost is primarily limited to an individual's name, date of birth, social security number, in some cases their spouse's information, as well as some disability ratings. However, this information could still be of potential use to identity thieves and we recommend that all veterans be extra vigilant in monitoring for signs of potential identity theft or misuse of this information.
What is the Department of Veterans Affairs doing to insure that this does not happen again?
The Department of Veterans Affairs is working with the President's Identity Theft Task Force, the Department of Justice and the Federal Trade Commission to investigate this data breach and to develop safeguards against similar incidents. The Department of Veterans Affairs has directed all VA employees complete the "VA Cyber Security Awareness Training Course" and complete the separate "General Employee Privacy Awareness Course" by June 30, 2006. In addition, the Department of Veterans Affairs will immediately be conducting an inventory and review of all current positions requiring access to sensitive VA data and require all employees requiring access to sensitive VA data to undergo an updated National Agency Check and Inquiries (NACI) and/or a Minimum Background Investigation (MBI) depending on the level of access required by the responsibilities associated with their position. Appropriate law enforcement agencies, including the Federal Bureau of Investigation and the Inspector General of the Department of Veterans Affairs, have launched full-scale investigations into this matter.
Where can I get further, up-to-date information?
The Department of Veterans Affairs has set up a special website and a toll-free telephone number for veterans that features up-to-date news and information. Please check this webpage for further updates or call 1-800-FED-INFO (1-800-333-4636).
Page last updated, May 22, 2006
Labels: breach notification, health information, identity theft, incident, information breaches, laptop, law enforcement
![]()

The Canadian Privacy Law Blog is licensed under a
Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Canada License.



