The Canadian Privacy Law Blog: Developments in privacy law and writings of a Canadian privacy lawyer, containing information related to the Personal Information Protection and Electronic Documents Act (aka PIPEDA) and other Canadian and international laws.
Recent Posts
- This blog has moved
- Some thoughts on street photography
- RCMP changes rules for criminal records checks
- Saskatchewan amends privacy regs to permit solicia...
- US Federal judge declares warrantless wiretapping ...
- Commisser releases discussion paper on cloud compu...
- Heathrow worker given police warning for body scan...
- How Privacy Vanishes Online, a Bit at a Time
- Facebook plans to allow users to "share" location
- Drawing the curtain on ISP cooperation with law en...
On Twitter
About this page and the author
 The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
For full contact information and a brief bio, please see David's profile.
Please note that I am only able to provide legal advice to clients. I am not able to provide free legal advice. Any unsolicited information sent to David Fraser cannot be considered to be solicitor-client privileged.
Privacy Calendar
Archives
- January 2004
- February 2004
- March 2004
- April 2004
- May 2004
- June 2004
- July 2004
- August 2004
- September 2004
- October 2004
- November 2004
- December 2004
- January 2005
- February 2005
- March 2005
- April 2005
- May 2005
- June 2005
- July 2005
- August 2005
- September 2005
- October 2005
- November 2005
- December 2005
- January 2006
- February 2006
- March 2006
- April 2006
- May 2006
- June 2006
- July 2006
- August 2006
- September 2006
- October 2006
- November 2006
- December 2006
- January 2007
- February 2007
- March 2007
- April 2007
- May 2007
- June 2007
- July 2007
- August 2007
- September 2007
- October 2007
- November 2007
- December 2007
- January 2008
- February 2008
- March 2008
- April 2008
- May 2008
- June 2008
- July 2008
- August 2008
- September 2008
- October 2008
- November 2008
- December 2008
- January 2009
- February 2009
- March 2009
- April 2009
- May 2009
- June 2009
- July 2009
- August 2009
- September 2009
- October 2009
- November 2009
- December 2009
- January 2010
- February 2010
- March 2010
- April 2010
Links


Blogs I Follow
Small Print
The views expressed herein are solely the author's and should not be attributed to his employer or clients. Any postings on legal issues are provided as a public service, and do not constitute solicitation or provision of legal advice. The author makes no claims, promises or guarantees about the accuracy, completeness, or adequacy of the information contained herein or linked to. Nothing herein should be used as a substitute for the advice of competent counsel.
This web site is presented for informational purposes only. These materials do not constitute legal advice and do not create a solicitor-client relationship between you and David T.S. Fraser. If you are seeking specific advice related to Canadian privacy law or PIPEDA, contact the author, David T.S. Fraser.
Monday, June 11, 2007
Choicepoint almost regains pre-breach value
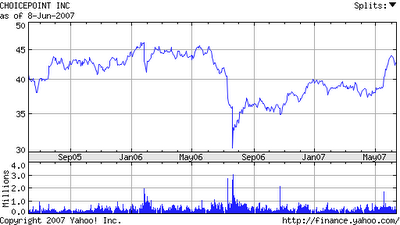 Though this article from Yahoo! Business is not about the privacy problems that plagued ChoicePoint and that made the company the poster boy for privacy breaches, I found it interesting to take a look at the chart of the company's stock value. In the last twelve months, the company's share value has slowly increased to barely recover the value lost by the high-profile breach. The total value lost between then and now is staggering.
Though this article from Yahoo! Business is not about the privacy problems that plagued ChoicePoint and that made the company the poster boy for privacy breaches, I found it interesting to take a look at the chart of the company's stock value. In the last twelve months, the company's share value has slowly increased to barely recover the value lost by the high-profile breach. The total value lost between then and now is staggering.
See: Out of the Gate: ChoicePoint Jumps: Financial News - Yahoo! Finance.
Labels: choicepoint, privacy
Friday, June 01, 2007
ChoicePoint Settles Data Security Case
Choicepoint, the poster child of security breaches, reportedly has settled with the Attorneys General of 44 states. The settlement is nominal cash-wise ($500,000) and includes requirements for tougher security measures:
ChoicePoint Settles Data Security Case - New York TimesJune 1, 2007
ChoicePoint Settles Data Security Case
By REUTERS
ChoicePoint has settled with 44 states over a data breach that potentially gave criminals access to personal information from more than 145,000 consumers.
The company agreed to adopt stronger security measures and pay $500,000 to the states, Richard Blumenthal, the attorney general of Connecticut, said yesterday.
ChoicePoint, which sells information about consumers to employers, marketers and others, said in 2005 that criminals posing as legitimate businesses had gained access to consumer data, including Social Security numbers and credit histories.
The company, based in Alpharetta, Ga., was one of several to announce large-scale security breaches in 2005, raising identity theft as an issue for many legislators and regulators.
ChoicePoint characterized the settlement as “fair and reasonable.”
In January 2006, ChoicePoint settled a case with the Federal Trade Commission involving the security breach.
Labels: choicepoint, identity theft, privacy
Monday, December 11, 2006
FTC to begin compensating ChoicePoint breach
The US Federal Trade Commission has finally begun the process to compensate victims of ChoicePoint's enormous data breach. Only those who ultimately were victims of fraud are being compensated, excluding those whose data was merely leaked:
FTC to Reimburse ChoicePoint Victims: Financial News - Yahoo! Finance:FTC Mails Claim Forms to 1,400 ChoicePoint Victims
WASHINGTON (AP) -- Victims of identify theft stemming from a security lapse last year at consumer data provider ChoicePoint Inc. can seek reimbursement from a $5 million fund set up to recoup their losses, the Federal Trade Commission said Wednesday.
Alpharetta, Ga.-based ChoicePoint collects, sells access to and analyzes information on consumers. The company agreed Jan. 26 to pay the FTC $15 million to settle charges that the company's security and record-handling procedures violated consumers' privacy rights when thieves infiltrated the company's massive database.
Identity thieves gained access to ChoicePoint's database by posing as small business customers, possibly compromising the personal information of 163,000 Americans, according to the FTC.
The settlement included a $10 million fine -- the agency's largest ever -- and $5 million for a victims' fund that will be used to reimburse those who file claims.
Labels: choicepoint, privacy
Friday, November 17, 2006
The rehabilitation of ChoicePoint
Last Saturday's New York Times ran a lengthy article on the rehabilitation of ChoicePoint. The one-time poster child for privacy fiascos has since apparently cleaned up its act. Now members of the "privacy possee" are quoted as singing the company's praises after it gots its house in order. Right after the high-profile privacy breach, representatives of the company contacted members of the privacy community (I even got a call) to ask what they did right and what they did wrong in responding to the incident. Since then, many of their harshest critics hail the company as a model for the data brokerage industry. Check it out: Keeping Your Enemies Close - New York Times.
The article also has a great timeline illustrating the number and magnitude of privacy incidents in the US over the past few years:
Labels: choicepoint, privacy
Wednesday, September 20, 2006
ChoicePoint victims uncompensated despite $5M fund
The Associated Press is reporting that months after a $5 million settlement assembled a pool of funds to compensate people for the ChoicePoint breach, nobody has seen a penny. "It's under review." See: AP: FTC yet to pay ChoicePoint victims - Yahoo! News.
Labels: choicepoint, privacy
Wednesday, August 23, 2006
Privacy hall of shame
Wired News: Privacy Debacle Hall of Fame10. ChoicePoint data spill
9. VA laptop theft
8. CardSystems hacked
7. Discovery of data on used hard drives for sale
6. Philip Agee's revenge
5. Amy Boyer's murder
4. Testing CAPPS II
3. COINTELPRO
2. AT&T lets the NSA listen to all phone calls
1. The creation of the Social Security Number
The Wired article has more details on each of the above blunders.
Via Concurring Opinions and Rob Hyndman.
Labels: cardsystems, choicepoint, laptop, privacy
Friday, April 28, 2006
It's the cover-up, stupid
In the hundreds of security and privacy breaches reported in the last few years, the companies involved that have fared the best are those that have been forthcoming with information and appear to be genuinely interested in the well being of the people involved. (I say "appear to be" because it doesn't really have to be sincere, but it has to benefit the individual. Once you can fake sincerity, you've got it made.) Those that have fared the worst are those that lied, misled customers, otherwise tried to cover it up or trivialize the breach.
Accidents happen and any company that has customer data on hand is at risk, to some degree or another. No security system is perfect. The biggest consequence of a breach is probably not an award of damages from the court but the loss of trust of customers and other stakeholders. The senior director at Lexis Nexis is quoted in a recent Network World article (Disclosure meant less pain in data theft) as confirming this:
But when the damage became clear, LexisNexis made an immediate decision to be forthcoming and transparent about the breach, he said. "We tried to do the best job we could," he said.The company contacted all those who were affected by the attack using the framework of a California data security disclosure law passed in 2003 as a guide, Cronin said.
The law is catching up after the high-profile cases of last year, including ChoicePoint, a data broker that acknowledged divulging sensitive personal information to identity thieves posing as customers. So far in the U.S., 20 states have implemented notification laws, and a federal law is under consideration.
After the data breach, LexisNexis took several steps to implement stronger security, Cronin said. The company reviewed the security of all its Web applications and created new procedures for verifying customers with access to sensitive data, he said.
LexisNexis encouraged certain customers to sign up for anti-virus software. It revamped online security access, looking at password complexity and expiration times. The company also implemented measures to automatically detect anomalies in use of its products to identity potential security problems, Cronin said.
LexisNexis learned other lessons. Passwords are dead, Cronin said, and two-factor authentication is recommended. But front-door perimeter attacks are less likely than the persistent weak link: people.
Now ask yourself why ChoicePoint is synonymous with "privacy breach" and not Lexis Nexis.
Labels: breach notification, choicepoint, information breaches
Tuesday, April 11, 2006
ChoicePoint Announces New PATRIOT Act Compliance and OFAC Compliance Software
About 99% of this is marketing speak, but parts of this press release from ChoicePoint look interesting:
ChoicePoint Announces New PATRIOT Act Compliance and OFAC Compliance Software:New Bridger Insight XG™ to Streamline Customer Screening
ALPHARETTA, GA (PRWEB) April 4, 2006 -- ChoicePoint today announced the official launch of Bridger Insight XG, a new Office of Foreign Asset Control (OFAC) and USA PATRIOT Act (PATRIOT Act) compliance solution. The new solution is now available to more than 4,000 existing Bridger Insight clients and other businesses across the banking and finance, insurance, securities, mortgage, automotive, gaming and public sectors.
Bridger Insight XG will reduce manual workload and streamline PATRIOT Act compliance and OFAC compliance workflow across an organization using new technologies designed to greatly simplify customer screening (including OFAC checks and ID verification) and due diligence processes. The new product is designed to help businesses more efficiently identify suspected terrorists and prevent crimes such as money laundering and ID theft.
Through new automated compliance workflow and case management tools, this new OFAC and PATRIOT Act compliance software can help users realize significant cost savings and greatly reduce false positive hits. Turn-key enterprise-wide deployment is another feature of the new software, which is equipped with the latest security and expanded audit capabilities.
Bringing extensive experience as a pioneer of OFAC compliance and PATRIOT Act compliance software, Bridger Insight XG helps clients make informed decisions, while saving time and reducing workload costs.
Bridger Insight solutions are used every day by the majority of the top 25 U.S. banks and thousands other businesses across the financial, insurance, securities, mortgage, automotive, gaming and public sectors to perform real-time and scheduled batch customer screening, utilizing more than 24 up-to-date watch lists, with access to extensive business and individual identity information, Factiva® Media and in-depth politically exposed persons databases.
More information about Bridger Insight XG can be obtained at www.BridgerInsight.com/XG.
Anyone know what a "in-depth politically exposed persons database" is? If so, leave a comment. Sounds interesting...
Labels: choicepoint, information breaches, patriot act
Sunday, February 26, 2006
Notification is the new moral imperative
Adam Shostack often has interesting things to say about privacy. He's posted, at Emergent Chaos, about the recent incident involving the University of Texas and their voluntary notice for the loss of encrypted patient information. Here Adam's take on their response:
Emergent Chaos: Analysis of University of Texas, 4,000 encrypted SSNs, Laptop:Since Choicepoint, there's been a dramatic shift in the way these incidents are perceived. Assertions of caring about privacy have transformed into a moral duty to report, even when the law doesn't require it. Work to undercut the 21 state laws in place by groups like the American Bankers Association misses the point. When there's a breach of personal data, the risk is on the citizen or consumer, not on the organization that lost control of the data. The organization has demonstrated that their risk management decisions don't have the results that customers want. That means the risk analysis must be done by the person, not the organization. For the person to do the risk analysis, they need to know what's happened.
We like transparency. We accept apologies (when they're not tortured or convoluted). We prefer to work with organizations that don't keep us in the dark, `for our own good.' Finally, we don't trust anyone who has lost control of data to get the next analysis right. Whatever bad laws happen to come out of Congress, there's a new social consensus, and the University did exactly the right thing.
Labels: breach notification, choicepoint, information breaches, laptop
Saturday, February 25, 2006
Cardsystems settles with the FTC
The US Federal Trade Commission has settled its complaint against CardSystems after a breach at the company comproised the personal information for forty million credit and debit card users. The company had, against its agreement with the card-issuers, kept information related to transactions it was processing and failed to secure it adequately.
Somewhat oddly, the LA Times article says that the FTC could not levy any civil damages or penalties, as it did with ChoicePoint, without mentioning why.
CardSystems Settles ChargesFrom Associated Press
February 24 2006
WASHINGTON — A data breach that left 40 million customer accounts vulnerable to hackers will lead to tighter security measures to protect millions of credit and debit card users, Federal Trade Commission officials said Thursday.
CardSystems Solutions Inc. has settled charges that the company broke the law by failing to ensure adequate safeguards for sensitive customer information. The breach resulted in millions of dollars in fraudulent purchases, the commission said.
The settlement calls for better safeguards to protect consumer data.
The FTC could not seek civil penalties under the law it accused CardSystems of violating.
Atlanta-based CardSystems processed credit card and other payments for banks and merchants. Last summer, it was disclosed that tens of millions of mostly MasterCard and Visa accounts were exposed to possible fraud after a hacker broke into the company's computer system.
"CardSystems kept information it had no reason to keep and then stored it in a way that put consumers' financial information at risk," FTC Chairwoman Deborah Platt Majoras said.
CardSystems' assets have since been bought by San Francisco-based Pay by Touch. The settlement requires Pay by Touch to implement a comprehensive security program and obtain independent audits every other year for 20 years.
Labels: cardsystems, choicepoint, information breaches
Thursday, January 26, 2006
Record, punitive fine for Choicepoint's data disaster
The FTC has imposed a record-breaking $10 million dollar penalty on ChoicePoint after the very high-profile incident that saw criminals obtain the personal information of 163,000 Americans. The FTC also ordered that the company pay an additional $5 million to compensate affected individuals.
This one incident has cost the company untold millions. They have paid lawyers, consultants, paid for credit monitoring for each affected individual, paid to deal with the investigation, paid to deal with the media, their share value has tanked and is only just recovering. I don't really think there is a better example for the proposition that bad security and bad privacy are bad for business.
Check out the FTC press release:
Choicepoint Settles Data Security Breach Charges; to Pay $10 Million in Civil Penalties, $5 Million for Consumer Redress:For Release: January 26, 2006
Choicepoint Settles Data Security Breach Charges; to Pay $10 Million in Civil Penalties, $5 Million for Consumer Redress
At Least 800 Cases of Identity Theft Arose From Company’s Data Breach
Consumer data broker ChoicePoint, Inc., which last year acknowledged that the personal financial records of more than 163,000 consumers in its database had been compromised, will pay $10 million in civil penalties and $5 million in consumer redress to settle Federal Trade Commission charges that its security and record-handling procedures violated consumers’ privacy rights and federal laws. The settlement requires ChoicePoint to implement new procedures to ensure that it provides consumer reports only to legitimate businesses for lawful purposes, to establish and maintain a comprehensive information security program, and to obtain audits by an independent third-party security professional every other year until 2026.
“The message to ChoicePoint and others should be clear: Consumers’ private data must be protected from thieves,” said Deborah Platt Majoras, Chairman of the FTC. “Data security is critical to consumers, and protecting it is a priority for the FTC, as it should be to every business in America.”
ChoicePoint is a publicly traded company based in suburban Atlanta. It obtains and sells to more than 50,000 businesses the personal information of consumers, including their names, Social Security numbers, birth dates, employment information, and credit histories.
The FTC alleges that ChoicePoint did not have reasonable procedures to screen prospective subscribers, and turned over consumers’ sensitive personal information to subscribers whose applications raised obvious “red flags.” Indeed, the FTC alleges that ChoicePoint approved as customers individuals who lied about their credentials and used commercial mail drops as business addresses. In addition, ChoicePoint applicants reportedly used fax machines at public commercial locations to send multiple applications for purportedly separate companies.
According to the FTC, ChoicePoint failed to tighten its application approval procedures or monitor subscribers even after receiving subpoenas from law enforcement authorities alerting it to fraudulent activity going back to 2001.
The FTC charged that ChoicePoint violated the Fair Credit Reporting Act (FCRA) by furnishing consumer reports – credit histories – to subscribers who did not have a permissible purpose to obtain them, and by failing to maintain reasonable procedures to verify both their identities and how they intended to use the information.
The agency also charged that ChoicePoint violated the FTC Act by making false and misleading statements about its privacy policies. Choicepoint had publicized privacy principles that address the confidentiality and security of personal information it collects and maintains with statements such as, “ChoicePoint allows access to your consumer reports only by those authorized under the FCRA . . . ” and “Every ChoicePoint customer must successfully complete a rigorous credentialing process. ChoicePoint does not distribute information to the general public and monitors the use of its public record information to ensure appropriate use.”
The stipulated final judgment and order requires ChoicePoint to pay $10 million in civil penalties – the largest civil penalty in FTC history – and to provide $5 million for consumer redress. It bars the company from furnishing consumer reports to people who do not have a permissible purpose to receive them and requires the company to establish and maintain reasonable procedures to ensure that consumer reports are provided only to those with a permissible purpose. ChoicePoint is required to verify the identity of businesses that apply to receive consumer reports, including making site visits to certain business premises and auditing subscribers’ use of consumer reports.
The order requires ChoicePoint to establish, implement, and maintain a comprehensive information security program designed to protect the security, confidentiality, and integrity of the personal information it collects from or about consumers. It also requires ChoicePoint to obtain, every two years for the next 20 years, an audit from a qualified, independent, third-party professional to ensure that its security program meets the standards of the order. ChoicePoint will be subject to standard record-keeping and reporting provisions to allow the FTC to monitor compliance. Finally, the settlement bars future violations of the FCRA and the FTC Act.
This case is being brought with the invaluable assistance of the U.S. Department of Justice and the Securities and Exchange Commission.
The Commission vote to accept the settlement was 5-0.
NOTE: A stipulated final judgment and order is for settlement purposes only and does not constitute an admission by the defendant of a law violation. Consent judgments have the force of law when signed by the judge.
Also check out:
- FTC imposes $10M fine against ChoicePoint for data breach - Computerworld
- FTC fines ChoicePoint over data breach
- Security Fix - Brian Krebs on Computer and Internet Security - (washingtonpost.com)
- U.S. Settles With Company on Leak of Consumers' Data - New York Times
UPDATE: Added NYT link (20060127)
Labels: choicepoint, identity theft, information breaches
Monday, January 23, 2006
Techniques of the phone record brokers
Paul McNamara in Network World writes about how companies that sell phone records get the info. Apparently, many use the little info they collect to get a fuller profile on ChoicePoint or Lexis. With all that info, they can fool customer service reps into believing they are dealing with the actual customer. Some use corrupt phone company employees, some of whom advertise their availability on websites frequented by the record brokers. Check it out: How phone records are stolen
Labels: choicepoint, information breaches
Saturday, December 24, 2005
Handle your incident well and good publicity may follow
Being involved in an incident in which the records of two million customers go astray is not at all pleasant. But the good news is that, if you handle it right, you may actually get some good publicity. Case in point:
Three Cheers for ABN - Yahoo! News:... So now for the good news: ABN AMRO is run by a bunch of standup folks, and the gents at DHL aren't far behind. True, I could criticize ABN for failing to, say, task a VP to personally cart its data tapes from warehouse to warehouse, and for instead shipping this valuable information like so many pounds of unwanted fruitcake. I could also place DHL in the same butterfingers basket at UPS. But in honor of the holiday season, I'll say instead what these companies did right.
DHL, for its part, upon learning on Nov. 18 that a data tape had gone missing, left no stone unturned trying to find it -- and ultimately did find it after a monthlong search. ABN gets credit for helping in the search and for (relatively) quickly informing its at-risk customers of the loss. But ABN gets extra credit for what it did after DHL found the tape.
Although the package containing the data tape was discovered apparently unopened, ABN volunteered to pay for one full year of credit monitoring for each of its 2 million clients who might conceivably have had their data compromised. That beats out Citigroup's June offer by 275 days, and it matches the offers from Ameritrade, ChoicePoint, and Reed.
Finally, ABN has determined that it will not let this situation ever happen again. For here on out, the company announced last week that it will discontinue outsourced shipping of sensitive personal data on tapes and switch to using only encrypted electronic means to transfer such data. Welcome to the 21st century, ABN. I just wish you had more company.
Labels: choicepoint, information breaches
Tuesday, December 20, 2005
Data Privacy Issues to Persist Next Year
On the data privacy front, the new year will bring more of the same, according to eWeek:
Data Privacy Issues to Persist Next Year:"People may remember 2005 as the year that corporate America woke up to the problem of data breaches and the importance of data privacy. Data leaks at Bank of America Corp., LexisNexis' Seisint division, ChoicePoint Inc. and CardSystems Inc. fed headlines for months, spawned countless lawsuits on behalf of aggrieved consumers and provided the impetus for federal legislation--still pending--to protect consumer data. But what will 2006 bring?
More of the same, say leading security experts.
More than ever before, enterprise IT managers will have to fight a battle on two fronts next year. On one side, more sophisticated and targeted attacks from organized, online criminal groups will test networks in new ways that are hard to detect...."
Labels: cardsystems, choicepoint, information breaches
Wednesday, December 07, 2005
Cornell University outlines security and privacy incident response plans
In response to a new New York law that requires notification of security and privacy breaches, Cornell University has issued the following media release outlining their plans for compliance:
Cornell complies with new state law on notification about stolen data:By Bill Steele
If someone hacks into a Cornell University computer and pulls out personal and private information about members of the Cornell community, the people whose data has been compromised will be notified promptly, according to Cornell Information Technologies and the University Counsel's office.
Although the exact procedures have not been worked out, notification would be by ordinary mail, according to Norma Schwab, associate university counsel. E-mail notification, she said, is not legally adequate and might be unreliable, especially in an age when users are bombarded with "phishing" messages with subject lines like "your account has been compromised."
The notification plan is being developed by an ad hoc group called the Data Incident Response Team, which includes members from the Office of Information Technologies, the Office of University Counsel, Cornell Police and the University Audit Office. The group meets periodically to consider data security policy and comes together whenever there is a concern that sensitive data may have been accessed.
The action is in response to a New York state law, the Information Security Breach and Notification Act, passed in August and going into effect Dec. 8. The law requires any business -- including nonprofits -- that maintains personal and private data to provide notification when its systems are invaded and there is a reasonable belief that personal information might have been revealed. The kinds of data involved include Social Security and driver's license numbers and credit card information, and the notification requirement is intended to help consumers fend off possible identity theft.
"It made sense that we should let people know that we are complying with the new law," said Steve Schuster, director of information security. Schuster said he plans to take advantage of the opportunity to make Cornell staff more aware of their responsibilities to protect sensitive data.
"We're still in a state where our data resides in a lot of different areas," he explained. "We all have to take responsibility for it." In other words, sensitive information is not all on one university mainframe, but may also be on ordinary desktop computers in various departments. Schuster plans to require that all new staff members receive a policy and practices briefing -- a short version of the Travelers of the Electronic Highway course required for new students -- before they are issued net IDs. He hopes eventually to set up some sort of annual review of security procedures for all staff. For nontechnical staff, security measures include using strong passwords, protecting those passwords from disclosure and physically securing the computer.
University policies on security are being updated. The venerable Responsible Use of Electronic Communications policy is being expanded as Responsible Use of Information Technology Resources, and it will incorporate policies on data management and security. Data will be broken into three categories: regulated information for which state and federal laws require security, such as Social Security numbers and grades; "Cornell confidential" information, such as salaries and performance reviews; and public data. Security should be tailored to the level of confidentiality of the data. "It will be necessary for departments to inventory where these data reside in their systems," Schuster said.
Despite having very talented people around, higher education institutions are not immune to security breaks, Schuster pointed out. "In the first six months of 2005 there were 72 media-worthy computer compromises in the United States," he reported, "and slightly over half of them were in higher ed. We deal with break-ins here all the time, but we have a really good process in place."
The New York law, patterned on one passed about two years ago in California, was inspired by several incidents in which large corporate databases were compromised. In the most widely publicized case, ChoicePoint, a credential-verifying firm, allowed criminals to obtain personal data on some 140,000 people. At least 15 states have passed similar laws, and legislation is pending at the federal level.
Labels: breach notification, cardsystems, choicepoint, identity theft, information breaches
Saturday, December 03, 2005
ChoicePoint in the spotlight again; seeking access to California drivers' records on behalf of DHS
The Los Angeles Times is reporting that the embattled ChoicePoint has garnered some additional publicity as it seeks to have access to the entire database maintained by the California Department of Motor Vehicles. It is seeking to have the usual DMV fees waived as it is seeking the records in order to serve its client, the Department of Homeland Security. A number of Californians are a little reluctant to have the state give access to the company that allowed identity thieves free rein in its other databases. The article also discusses some tussles with the Pennsylvania DMV. Check it out: Big Data Broker Eyes DMV Records - Los Angeles Times.
Thanks to Daniel Solove at Concurring Opinions for the link. Check out what he has to say as well: Concurring Opinions: ChoicePoint Wants Your Motor Vehicle Records.
Labels: choicepoint, homeland security, information breaches
Saturday, November 19, 2005
The Rootkit of All Evil
Dan Mitchell at the New York Times sums up some lessons learned from the Sony rootkit fiasco: The Rootkit of All Evil - New York Times. The same lessons apply for privacy problems (see Choicepoint, especially): "One, bloggers will catch you. And two, it's not the screw-up, it's the cover-up."
Labels: choicepoint, information breaches
Saturday, November 12, 2005
ChoicePoint sells access to FBI and Pentagon to track terrorists and others
According to GovExec.com, a Freedom of Information Act request has revealed that embattled ChoicePoint has been providing extensive services to the FBI and the Defense Department, essentially providing access to its enormous databases that the US government would not be able to compile on its own.
www.GovExec.com - FBI, Pentagon pay for access to trove of public records (11/11/05):"To help the government track suspected terrorists and spies who may be visiting or residing in this country, the FBI and the Defense Department for the past three years have been paying a Georgia-based company for access to its vast databases that contain billions of personal records about nearly every person -- citizens and noncitizens alike -- in the United States.
According to federal documents obtained by National Journal and Government Executive, among the services that ChoicePoint provides to the government is access to a previously undisclosed, and vaguely described, 'exclusive' data-searching system. This system in effect gives law enforcement and intelligence agents the ability to use the private data broker to do something that they legally can't -- keep tabs on nearly every American citizen and foreigner in the United States."
Thanks to beSpacfic for the link: beSpacific: Gov't Pays Aggregator for Access to Extensive Database of Personal Info.
Labels: choicepoint, information breaches, law enforcement
Tuesday, November 08, 2005
ChoicePoint filing suggests further 17,000 affected consumers
ChoicePoint's most recent 10-Q filing with the SEC suggests that an additiona 17,000 consumers were affected by the high-profile data breach. See: ChoicePoint filing: 17,000 more may be fraud victims - 2005-11-08.
It's interesting to look at the filing itself, just to get a flavour of the cost of this issue to ChoicePoint and its impact upon their bottom line:
CHOICEPOINT INC (Form: 10-Q, Received: 11/08/2005 15:01:50):Fraudulent Data Access
ChoicePoint’s review of the Los Angeles fraudulent data access described in the Company’s Form 10-K for the year ended December 31, 2004 and other similar incidents is ongoing. The Company currently expects that the number of consumers to which it will send notice of potential fraudulent data access will increase from the approximately 162,000 consumers it has notified to date, but the Company does not anticipate that the increase will be significant.
As previously disclosed in the Company’s Form 10-K for the year ended December 31, 2004, ChoicePoint is continuing to strengthen its customer credentialing procedures and is recredentialing components of its customer base, particularly customers that have access to products that contain personally identifiable information. Further, the Company continues to review and investigate other matters related to credentialing and customer use. The Company’s investigations as well as those of law enforcement continue. The Company believes that there are other instances that will likely result in notification to consumers. As previously stated, the Company intends for consumers to be notified, irrespective of current state law requirements, if it is determined that their sensitive personally identifiable information has been acquired by unauthorized parties. The Company does not believe that the impact from notifying affected consumers will be material to the financial position, results of operations or cash flows of the Company.
On March 4, 2005, ChoicePoint announced that the Company will discontinue the sale of certain information services that contain sensitive consumer data, including social security numbers, except (1) where there is either a specific consumer driven transaction or benefit, or (2) where such services serve as authentication or fraud prevention tools provided to large accredited customers with existing consumer relationships, or (3) where the services support federal, state or local government and law enforcement purposes. The Company cannot currently accurately estimate the future impact that the customer fraud, related events and the decision to discontinue certain services will have on our operating results and financial condition. The Company will review various technology investments in this small business segment as well as other related costs incurred in serving this segment.
ChoicePoint incurred $5.4 million ($3.3 million net of taxes) in the first quarter of 2005, $6.0 million ($3.7 million net of taxes) in the second quarter of 2005, and $4.0 million ($2.5 million net of taxes) in the third quarter of 2005 for specific expenses related to the fraudulent data access previously disclosed. Approximately $2.0 million of the $15.5 million total charges through September 30, 2005 were for communications to, and credit reports and credit monitoring for, individuals receiving notice of the fraudulent data access and approximately $13.5 million for legal expenses and other professional fees. The Company currently estimates that it will incur additional incremental expenses as a result of the fraudulent data access of approximately $3 to $5 million in the fourth quarter of 2005. In addition, the publicity associated with these events or changes in regulation may materially harm the business and ChoicePoint’s relationship with customers or data suppliers.
The Company is involved in several legal proceedings or investigations that relate to these matters, as described in “Legal Proceedings” of this Form 10-Q. ChoicePoint is unable at this time to predict the outcome of these actions. The ultimate resolution of these matters could have a material adverse impact on the financial results, financial condition, and liquidity and on the trading price of the Company’s common stock. Regardless of the merits and ultimate outcome of these lawsuits and other proceedings, litigation and proceedings of this type are expensive and will require that substantial Company resources and executive time be devoted to defend these proceedings.
Security Breaches and Misuse of Information Services
Security breaches in the Company’s facilities, computer networks, and databases may cause harm to ChoicePoint’s business and reputation and result in a loss of customers. Many security measures have been instituted to protect the systems and to assure the marketplace that these systems are secure. However, despite such security measures, the Company’s systems may be vulnerable to physical intrusion, computer viruses, attacks by hackers or similar disruptive problems. Users may also obtain improper access to the Company’s information services if they use stolen identities or other fraudulent means to become ChoicePoint customers or by improperly accessing ChoicePoint’s information services through legitimate customer accounts. If users gain improper access to ChoicePoint’s databases, they may be able to steal, publish, delete or modify confidential third-party information that is stored or transmitted on the networks. A security or privacy breach may affect ChoicePoint in a variety of ways, including but not limited to, the following ways:
- deterring customers from using ChoicePoint’s products and services or resulting in a loss of existing customers;
- deterring data suppliers from supplying data to the Company;
- harming the Company’s reputation;
- exposing ChoicePoint to litigation and other liabilities;
- increasing operating expenses to correct problems caused by the breach;
- affecting the Company’s ability to meet customers’ expectations;
- causing inquiry from governmental authorities; or
- legislation that could materially affect the Company’s operations.
The Company expects that, despite its ongoing efforts to prevent fraudulent or improper activity, in the future it may detect additional incidents in which consumer data has been fraudulently or improperly acquired. The number of potentially affected consumers identified by any future incidents is obviously unknown. "
Labels: breach notification, choicepoint, information breaches
Friday, November 04, 2005
US parties split on proposed data protection and notification laws
The Washington Post is continuing to chronicle the ongoing debate between the US political parties on proposals to implement a federal privacy law to protect consumers against indentity theft. Privacy advocates are very concerned that the process will result in a weak law that pre-empts much more rigorous state laws, such as that in California. The California law is largely responsible for the wave of publicity about privacy breaches in the last year.
Parties Split on Data-Protection Bill:"... Under the bill, data brokers and other firms that store consumer data would have to notify consumers that their information was breached only when it was determined that a 'significant risk' of identity theft or other fraud might result.
That decision would be made by the company that was breached, which Democrats said was akin to having to no requirement at all.
This year alone, tens of millions of consumers have been notified of breaches at information brokers such as ChoicePoint Inc. and LexisNexis, financial institutions, government agencies, universities, online retailers and other firms.
Many notices were sent out under a California law that covers any firm doing business in the state.
'No notices would have gone out under the standard put forth in this bill,' which would preempt state laws, said Rep. Janice D. Schakowsky (D-Ill.). 'We would not have known how badly corporations treat personal information, nor would consumers have been able to take action to protect themselves -- even from financial identity theft -- if this bill had been in place in February 2005.'
Data brokers, direct marketers, financial institutions and several large technology companies supported the approach of the bill, as did FTC Chairman Deborah P. Majoras. They argue that thieves or hackers cannot always use data they might gain access to, and that bombarding consumers with notices every time a breach occurs would cause people to ignore them...."
Labels: breach notification, choicepoint, identity theft, information breaches
Saturday, October 29, 2005
Responding to a security breach
NetworkWorld has a great article on how to respond to security incidents involving personal or corporate data:
Responding to a security breach...But organizations can reduce their overall losses by reporting breaches in a timely manner and offering whatever help they can to the affected parties, Penn says. On the other hand, organizations can compound their losses by covering up and delaying reporting, such as the case with ChoicePoint, whose stock dropped by 15% after fraud in its system exposed 145,000 credit identities in February. And health maintenance organization Kaiser Permanente was fined $200,000 in August for a three-month delay in reporting an exposure of patient data posted on a publicly accessible Web site used for help desk support....
Labels: choicepoint, information breaches
Friday, October 07, 2005
ChoicePoint Struggles to Strike Balance
The pendulum has swung the other way and some customers of ChoicePoint are a little upset at how vigilant the company is being about how it screens its customers. Even law enforcement agencies are being subjected to random audits and on-site inspections: RedNova News - Technology - ChoicePoint Struggles to Strike Balance.
Labels: choicepoint, information breaches
Saturday, September 17, 2005
ChoicePoint alleges misuse of its data, alerts affected consumers
ChoicePoint has recently fingered employees of four of its significant customers for likely misusing the company's massive databases. The most significant incident relates to an employee of the Miami Dade police department, who gained access to records of over four thousand individuals. ChoicePoint is holding up its auditing tools for successfully determining the misuse of data by employees of legitimate users and has begun to notify the affected consumers. See: Florida cop misused data, ChoicePoint claims - Consumer Security - MSNBC.com.
Labels: choicepoint, information breaches
Saturday, September 10, 2005
US Panel agrees that government needs new rules and guidelines for use of private data resources
The US Department of Homeland Security convened a two-day workshop on privacy, which wrapped up yesterday. Among the outcomes was an apparent consensus among panelists that new rules and guidelines are required for US government use of personal information, particularly the government's use of private sector information providers like ChoicePoint and Acxiom. See: Panel: New rules, tech needed for data privacy | CNET News.com.
More from Government Computer News:
Task force: IT systems' design should incorporate privacy safeguards:"By Alice Lipowicz
Contributing Staff Writer
New IT tools such as data mining ought to be used for homeland security only if their intrusiveness on privacy and infringement of due process rights can be adequately addressed in advance, according to a new report from a task force sponsored by the New America Foundation, a Washington-based think tank.
The task force of academics examined technologies including data mining, link analysis, data integration and biometrics, and recommended that they be deployed in efforts to counteract terrorism “if and only if” privacy protections are in place. It also suggested principles to follow to ensure the protections...."
Labels: choicepoint, information breaches
ChoicePoint unit to help in Katrina recovery efforts
ChoicePoint's press coverage has been uniformly negative, but it appears that the company and a subsidiary will be called upon to help in a number of ways in the wake of Hurricane Katrina. A subsidiary, Bode Technologies, will be assisting in the DNA analysis to identify victims, while ChoicePoint's databases will be used by evacuees who don't have identitication documents to prove who they are. See: ChoicePoint unit to help identify dead.
Labels: choicepoint, information breaches
Thursday, September 01, 2005
ChoicePoint says it's securing public's data better
In an interview with Cox News Service, ChoicePoint's Chief Privacy Officer, Carol DiBattiste, says that the company has made great strides in securing the information that it holds but can't guarantee that everything's perfect: Macon Telegraph | 09/01/2005 | ChoicePoint says it's securing public's data better.
Labels: choicepoint, information breaches
Wednesday, August 31, 2005
New charges in ChoicePoint case
A grand jury in Los Angeles has returned a new indictment against Olatunji Oluwatosin, charging the man with twenty-two counts of identity theft and other miscellaneous crimes in connection with the very high profile ChoicePoint breach. This indictment replaces the previous one, which included only four counts of identity theft. In February, Oluwatosin pleaded "no contest" to one charge of identity theft and is presently serving a sixteen month sentence.
More info: New charges in ChoicePoint identity theft case - Consumer Security - MSNBC.com.
Labels: choicepoint, identity theft, information breaches
Sunday, August 14, 2005
Man Faces More Charges in Fraud Scheme
The only person criminally charged in connection with the ChoicePoint fiasco and the resultant fraud is now facing additional charges of identity theft, according to the Associated Press (via The Washington Post): Man Faces More Charges in Fraud Scheme.
Labels: choicepoint, identity theft, information breaches
Thursday, August 11, 2005
ChoicePoint SEC investigation may widen
The US Securities and Exchange Commission is looking into stock sales made by executives at ChoicePoint which were made after they became aware of he massive security/privacy incident, but before it was made public. The SEC's probe has been escalated the "informal inquiry" to a full-blown investigation. See: HoustonChronicle.com - ChoicePoint investigation may widen.
Labels: choicepoint, information breaches
Tuesday, August 09, 2005
Security, Identity Theft and Credit Professionals
Security, Identity Theft and Credit Professionals
David T.S. Fraser†
The credit industry in North America has recently found itself both in the spotlight and the legal crosshairs, primarily due to two factors: privacy laws and identity theft. Both demand increased vigilance on the part of credit grantors to protect both their customers and complete strangers from identity theft.
In March of this year, the spotlight turned to the industries that rely on or traffic in personal information. A number of high profile personal information leaks wound up on the front pages of newspapers in Canada and the United States. In the US, scammers gained access to the personal information of 310,000 individuals via a Lexis-Nexis subsidiary, Seisint.[1] One of the largest American data aggregators, ChoicePoint, was similarly scammed, leading to the disclosure of personal information on 1.2 million Americans.[2] The Bank of America lost a set of backup tapes containing sensitive credit information of thousands of US government employees.[3] In Canada, we have had similar information breaches; the highest profile being the accidental faxing of information from CIBC branches to a junkyard in West Virginia. [4] In addition, police in Alberta this past winter were shocked to discover piles of credit reports on senior provincial bureaucrats at a methamphetamine lab, leading to the finding that drug addicts are being hired by identity thieves to “dumpster dive” for such information. [5] Hand in hand with these incidents, the crime of identity theft[6] continues to increase. This species of fraud is said to be the fasted growing crime on the continent.
The result of this has been significantly increased customer awareness of industries that otherwise operated in the background. Also, lawmakers have turned their legislative agendas toward increased regulation and accountability in this area. A number of remedial bills are currently pending before the U.S. Congress while commentators have suggested that Canada’s private sector privacy laws are not up to the task of dealing with incidents such as this. A private member’s bill introduced in the Ontario legislature would require companies to notify all individuals whose information is inappropriately accessed. [7] Stronger remedies will likely be on the agenda when the Personal Information Protection and Electronic Documents Act comes up for review in Parliament next year.
Class action lawyers and the courts are not waiting for the legislators to catch up to the current situation. In April, the Michigan Court of Appeals upheld a class action lawsuit that found a trade union liable for inappropriate security of personal information after the information was used for identity theft. [8] Class action lawyers have commenced litigation against CIBC as a result of the faxing incidents[9]. The Michigan case related to actual identity theft that had occurred. The CIBC case alleges that the bank should be responsible for the increased vigilance required to protect the individuals against identity theft and for the increased likelihood that they may be subject to identity theft. It will not be long before individuals whose identities are stolen will seek recourse against the credit grantors who offered facilities to the impostors, arguing that they did not do enough to verify the identity of the person seeking credit. These plaintiffs will be seeking damages related to the cost of repairing their credit, which can run pretty steep.
What does this all mean to credit grantors? Anybody in possession of information that would be useful to commit identity theft has an obligation to protect it from being inappropriately used or otherwise compromised. This obligation is already set out in PIPEDA and the common law will likely also impose a duty of care where the risk of identity theft is foreseeable. (In the current climate, it would be difficult to argue that it is not foreseeable.)
Custodians of personal information may have a legal duty to inform individuals if their information is compromised. This obligation may be statutory if the private members bill in Ontario becomes law, or may be imposed by the courts if a duty of care and a standard of care in negligence is established. Individuals whose information is compromised should be given the opportunity to keep a watch on their credit reports. If they are not informed of the situation, they will have no such warning.
Finally, credit grantors have to be even more vigilant in establishing the identities of those to whom they extend credit. This is not only to protect against credit losses, but to reduce the likelihood that your company will be the subject of privacy complaints and litigation. In this effort, privacy laws pull credit grantors in two different directions. On one hand, grantors should clearly establish the identity of any applicant. On the other hand, they can only require information that is reasonably necessary for the articulated purpose. To satisfy both, credit grantors should establish clear and reasonable policies related to how they will verify identity. Requiring two pieces of government issued identification, with at least one or both containing the applicant’s current address and photo would appear to be reasonable. The adoption of privacy best practices, including greater security and identify verification, can decrease the legal and credit risk faced by credit grantors. The courts and the legislators see that custodians of sensitive information are part of the problem. Being part of the solution makes business sense as well.
† David T.S. Fraser is the chairman of the privacy practice group at McInnes Cooper, Atlantic Canada’s largest single law partnership. He is also the principal legal advisor the National Privacy Services, a company that offers end-to-end training and compliance solutions to clients across Canada. He can be reached at david.fraser [at] mcinnescooper.com or (902) 424-1347.
[1] “LexisNexis begins notifying possible victims”, CNN International (19 April 2005). Online at http://edition.cnn.com/2005/TECH/04/19/lexisnexis.breach.ap/.
[2] “Database giant gives access to fake firms”, MSNBC.com (14 February 2005). Online at http://www.msnbc.msn.com/id/6969799/. [3] “Bank of America loses customer data”, MSNBC.com (1 March 2005). Online at http://www.msnbc.msn.com/id/7032779/.
[4] “CIBC faxes go to scrapyard”, The Globe and Mail (26 November 2004). Online at http://www.theglobeandmail.com/servlet
/story/RTGAM.20041126.wxcibc1126/BNStory/Business/.
[5] “Civil Servants See Red”, Edmonton Sun (14 November 2004).
[6] For the purpose of this article, “identity theft” means the fraudulent impersonation of an innocent third-party in order to obtain credit facilities and other benefits in the name of the victim.
[7] An Act to Amend the Consumer Reporting Act, Bill 174.
[8] Health Care Assn. Workers Comp. Fund v. Bureau of Workers Disability, (15 February 2005) Michigan Court of Appeals (Wayne Circuit), No. 246684.
[9] Statement of Claim is available online at http://www.cacounsel.com/CIBC%20Class%20Action%20Claim.pdf.
Labels: alberta, choicepoint, health information, identity theft, information breaches, privacy
Tuesday, July 26, 2005
Who's minding the store (of private data you gave up)?
Today's USA Today has an OP/ED on privacy and the little bits of data that consumers are willing to give up in exchange for a bit of convenience or a discount. There aren't any great revelations in the article, but it is an example of how the call for greater regulation is moving front and centre in the mainstream media:
USATODAY.com - Who's minding the store (of private data you gave up)?"Several recent developments have chipped away at privacy:
• Invisible surveillance. Information is increasingly collected without the knowledge, much less permission, of those giving it up. "Black boxes" the size of cigarette packs have been installed in 40 million vehicles to monitor speed, seat-belt use and more. Only five states require that car buyers be informed of its presence. From Philadelphia to Chicago to Los Angeles, surveillance cameras are on silent watch in public spaces. London's recent success in capturing photos of terrorists has fed the calls for more.
• Collection mania. Data mining is big business. Companies vacuum up data from public and private sources, aggregate it, analyze it and sell it to buyers ranging from private companies to the CIA. Any one item is not very invasive, but when birth certificates, credit histories, real estate deeds, military records and insurance claims are pulled together, they paint intimate pictures. If errors exist, the public has no way to know or demand fixes.
• Data thefts. In recent months, breaches involving banks, credit card processors, colleges and the biggest of the data brokers, ChoicePoint, have left millions of people vulnerable to identity theft. Legislators and the companies themselves have done little to correct the problem.
• Government mischief. Collection of information by the government is often fraught with errors and overreaching. The Transportation Security Administration's "no-fly" list has repeatedly ensnared innocent travelers. The agency was rapped again Friday for violating privacy while trying to create another program to screen fliers.
It's easy to sympathize with the goals of much of this data collection, whether safer driving or terrorism prevention. But it might be possible to reach those goals less invasively.
Congress and state lawmakers need to establish basic protections for all information. Businesses need to realize they can profit more by viewing consumers as partners, not as pesky subjects for dossiers. Individuals will need ways to monitor data about themselves.
Fighting technology is no answer. It won't work. Nor is surrendering to Big Brother. A palatable compromise should involve an active government, private ingenuity and an involved public. Perhaps that's what's finally taking off in Orlando."
Labels: choicepoint, identity theft, information breaches, surveillance
Thursday, July 21, 2005
Break-in costs ChoicePoint millions
The financials are in for ChoicePoint's second quarter and CNet is reporting that the data aggregator has taken a total charge fo $11M related to the privacy incident that took place some months ago. That's real money and has a direct impact on the shareholder's value:
Break-in costs ChoicePoint millions | CNET News.com:"Data broker ChoicePoint took a $6 million charge in its second quarter to cover costs related to the leak of information on about 145,000 Americans, it said Wednesday.
The charge is in addition to the $5.4 million in costs the company recorded in the first quarter. Of the total $11.4 million, about $2 million in charges through June 30 were for communications to individuals whose data has been exposed as well as credit reports and monitoring services for those people, the company said in a statement.
The remaining $9.4 million was for legal and other professional fees, ChoicePoint said...."
Labels: choicepoint, information breaches
Monday, July 18, 2005
"Dr. Busybody's" diabetic database
The New York Post isn't too keen on the proposed New York registry of diabetics (see The Canadian Privacy Law Blog: City Officials Aim to Track How Diabetics Manage Illness):
DR. BUSYBODY'S DATABASE - Yahoo! News:"... Name-specific registries for certain communicable diseases - such as HIV/AIDS and hepatitis - make sense.
The early-20th century Typhoid Mary demonstrated the need for public-health authorities to prevent individuals from spreading highly contagious diseases.
Diabetes doesn't fall into that category.
This would be the first time that a complete record would be assembled for a non-communicable, chronic affliction.
As far as privacy goes, Frieden notes that the confidentiality of the department's registries haven't been compromised in more than 140 years.
That anybody knows about, of course.
Indeed, the potential of large private databases being compromised by hackers and criminals is sharper than it's ever been - as demonstrated by the recent cases involving MasterCard and the ChoicePoint identification-and-verification service. And health-insurance companies and potential employers would have no interest in Frieden's database? Yeah, right.
It's time for New Yorkers to say enough is enough.
And if all this information depresses you, and drives you to drink? Well, expect a visit from Dr. Frieden presently.
He'll be there to help."
Labels: choicepoint, health information, information breaches
Saturday, July 16, 2005
A Pass on Privacy?
Recently, the writers of the Sunday New York Times have consistently had interesting things to say about privacy-related topics. This week, Christopher Caldwell talks about the creeping appearance of tracking technologies into daily lives and how their uses can be easily expanded:
A Pass on Privacy? - New York Times"Anyone making long drives this summer will notice a new dimension to contemporary inequality: a widening gap between the users of automatic toll-paying devices and those who pay cash. The E-ZPass system, as it is called on the East Coast, seemed like idle gadgetry when it was introduced a decade ago. Drivers who acquired the passes had to nose their way across traffic to reach specially equipped tollbooths -- and slow to a crawl while the machinery worked its magic. But now the sensors are sophisticated enough for you to whiz past them. As more lanes are dedicated to E-ZPass, lines lengthen for the saps paying cash.
E-ZPass is one of many innovations that give you the option of trading a bit of privacy for a load of convenience. You can get deep discounts by ordering your books from Amazon.com or joining a supermarket ''club.'' In return, you surrender information about your purchasing habits. Some people see a bait-and-switch here. Over time, the data you are required to hand over become more and more personal, and such handovers cease to be optional. Neato data gathering is making society less free and less human. The people who issue such warnings -- whether you call them paranoids or libertarians -- are among those you see stuck in the rippling heat, 73 cars away from the ''Cash Only'' sign at the Tappan Zee Bridge.
Paying your tolls electronically raises two worries. The first is that personal information will be used illegitimately. The computer system to which you have surrendered your payment information also records data about your movements and habits. It can be hacked into. Earlier this year, as many as half a million customers had their identities ''compromised'' by cyber-break-ins at Seisint and ChoicePoint, two companies that gather consumer records.
The second worry is that personal information will be used legitimately -- that the government will expand its reach into your life without passing any law, and without even meaning you any harm. Recent debate in Britain over a proposed ''national road-charging scheme'' -- which was a national preoccupation until the London Tube bombings -- shows how this might work. Alistair Darling, the transport secretary, wants to ease traffic and substitute user fees for excise and gas taxes. Excellent goals, all. But Darling plans to achieve them by tracking, to the last meter, every journey made by every car in the country. It seems that this can readily be done by marrying global positioning systems (with which many new cars are fitted) with tollbooth scanners. The potential applications multiply: what if state policemen in the United States rigged E-ZPass machines to calculate average highway speeds between toll plazas -- something easily doable with today's machinery -- and to automatically ticket cars that exceed 65 m.p.h.?..."
Labels: choicepoint, information breaches
Commentary: Verizon puts your privacy in precarious position
It is interesting how sensitive some are becoming to privacy issues. I don't think we would have seen a commentary like this one a year ago:
Connected: Verizon puts your privacy in precarious position"Would you give your credit card number to a company if you knew it was to be used for anything else besides taking your payment? That is exactly what is happening for thousands of people nationwide who have signed up for Verizon's VoiceWing Voice over IP telephone service.
VoiceWing is different from Verizon's traditional telephone service in several ways, one of which is that the company only accepts credit cards as payment. It will not direct bill you. So you must provide your card to get the service. Once you have the service, Verizon debits your card monthly -- and also uses the last four digits of your card number to verify who you are when you call for support.
According to Margo Hammar, chief privacy officer at Verizon, using your credit card digits this way is just like paying for your gas at the pump, then crumbling the receipt and throwing it away.
But it's not the same. At the pump, the credit card is inserted for a one-time transaction and not saved by the gas station. It is you who makes the decision on the spot to provide the card data; and it is you who decides whether to print the receipt and crumble it (or keep it). In the VoiceWing scenario, your credit card information is placed into a database at Verizon -- and then the last four digits are shown to any customer support rep who pulls up your record -- even if no transaction is taking place.
Hammar told me that "Verizon takes the safeguarding of client information very seriously" and that the company has created a method and procedure to be used by employees with a need to know. As the key privacy person, she has pushed the company to move away from using Social Security numbers for customer authentication, but has not yet provoked the company to stop using this credit card data for the same task.
According to Dean Ocampo, product marketing manager for security software developer Check Point Software Technologies, using only the last four digits minimizes risk compared to using the entire number, "but ideally you don't want to use any of it." He says the issue goes deeper than whether the company is using the digits. It involves the processes they employ and the depth of security.
In the Verizon situation, your credit card digits are displayed to first-tier customer support reps -- people who are not in a "need to know" position regarding your credit card. In one call that I made to VoiceWing support, I refused to give the CSR my digits, which made him exclaim that the digits are right in front of him already; it's not like I'm revealing anything new to him.
That, in fact, is the problem. The digits should not be in front of him. He has no reason to see a customer's credit card data, no matter how ethical he is. Check Point's Ocampo agrees: "The more you put private data through the company, the more likely it can be hacked and stolen." He cites instances in which companies have not properly secured the data at every juncture, even though it thinks it has. Recent news items about security problems at Citibank, ChoicePoint and CVS provide examples. Ocampo's examples include points of attach within the company, including PCs living around the perimeter of the network that have not been completely secure.
Since businesses make decisions over time, other factors may later create security risks. For instance, a move to outsourcing customer support offshore would put your credit card data in a rep's hands in another country -- perhaps a country that doesn't have the same protection laws that are in force in the United States. Securing customer privacy is not a science. What's good for the business is not always good for privacy, and vice versa. Companies are always dealing with the trade-offs when making business decisions.
Verizon's published privacy policy promises that the company will use SSL (a security mechanism) whenever it transmits your credit card, but it doesn't promise to use your card number only for your transactions. As long as Verizon continues to use customer credit card numbers as authentication, in whole or in part, it is putting the customer at risk, no matter how slight."
Labels: choicepoint, information breaches
Thursday, July 07, 2005
The Baseline Security Hall of Shame
Baseline Magazine, a publication of Ziff-Davis, is soliciting contributions for their new "Security Hall of Shame", which will be published in a special edition entitled "Year of Living Dangerously." They've already "inducted" a number of now companies in this article who have become notorious for incidents involving personal information:
The Baseline Security Hall of Shame
- Lowlight of the Month: CardSystems Solutions Inc.
- Other Hall of Shame Inductees
- Bank of America Corp.
- Choicepoint Inc.
- Citigroup
- DSW Shoe Warehouse (DSW Inc.)
- LexisNexis, a division of Reed Elsevier Inc.
- Polo of Ralph Lauren Media LLC
- Wachovia Corp.
Labels: cardsystems, choicepoint, information breaches
Wednesday, July 06, 2005
California Selects ChoicePoint to Develop Terrorist-Tracking Computer System
ChoicePoint has been awarded a contract by the California government to help track criminals and terrorists, despite protests from Californians: RedNova News - Technology - California Selects ChoicePoint to Develop Terrorist-Tracking Computer System.
Labels: choicepoint, information breaches
Sunday, July 03, 2005
ChoicePoint's IRS contract under review
ChoicePoint is back in the news. This time, it is because of a multi-million dollar contracted awarded to it by the IRS. The contract is now coming under review after widespread criticism: ChoicePoint's IRS contract under review.
Labels: choicepoint, information breaches
Friday, June 24, 2005
Q&A: ChoicePoint's Rich Baich on data breach, security needs
Computerworld has in interview with Rich Baich, the CISO of Choicepoint. I'm not sure whether observers will find it reassuring:
Q&A: ChoicePoint's Rich Baich on data breach, security needs - Computerworld:"You have in the past said that what happened at ChoicePoint was not really a security breach. Then what was it? It all comes down to how you define a breach and how you define an incident. This was fraud. Someone fraudulently provided authentication to the system. It's no different than credit card theft and credit card fraud. Those are never referenced as IT-related issues though they happen millions of times every year. In fraud terms, it's called an account takeover. And that's what occurred. All I was trying to do was educate the press more than anything else that this was not what everyone would call a traditional hack. "
Labels: choicepoint, information breaches
Tuesday, June 14, 2005
The Rising Threat from Bad Data
I have previously pointed to items addressing the issue of data quality and data aggregators, but this piece from Baseline Magazine shows a real human side of the potential consequences of bad data:
The Rising Threat from Bad Data:"Steven Calderon had a clean record, a clean conscience and no reason to think that his new employer's routine background check would cause any problem at all. Then the sheriff showed up at the office and took him to jail on warrants for child molestation and rape.
A nightmare? Sure, but Calderon figured it was a mistake that could be cleared up pretty quickly. He'd reported the theft of his Social Security number and birth certificate in 1993, so it was obvious that the bad guy was whoever had stolen Calderon's identity.
A week later he was still in jail, a victim of bad information from data broker ChoicePoint -- and of the blind belief held by his employer, the police and everyone else involved that he was more likely to be lying than the data was...."
Labels: choicepoint, information breaches
U.S. Offshoring of Personal Data Grows
Elites TV, a news source I've never heard of before, has a lengthy and negative article on offshoring of personal data processing.
U.S. Offshoring of Personal Data Grows - Elites TV - Your Elite News Source:"According to the Identity Theft Resource Center in San Diego, CA there have been close to 60 reported security breaches of customer financial information from United States corporations thus far in 2005, involving 13.5 million customers’ identities. The companies include Choicepoint, Inc., Bank of America Corp., Wachovia Corp., Ameritrade Holding Corp., DSW Shoe Warehouse, Time Warner Inc., LexisNexis and most recently Citbank Financial Group. While most lost data has involved data storage tapes lost in transit by courier services or UPS, others involved computer security breaches. And as corporate America looks for ways to shore up its security problems rather than face the wrath of Congress, an even more unwieldy problem is brewing abroad.
As holes still exist in protecting the personal information of both customers and employees of corporations in the United States, many of these same corporations, which include the largest financial institutions and two of the three credit reporting agencies, have offshored information technology units which include-back office functions from customer service to software development and engineering.
Yet American customers or consumers are never informed whether or not their personal information and credit history is being offshored, as it is not required by U.S. corporations to do so. Coming to light is that various U.S. government programs and states are utilizing more and more offshore subcontractors in addition to those corporate entities which indirectly do business with the U.S. government. But unknown to the American consumer or taxpayer is the threat of theft of an individual’s identity and financial resources which remain largely unprotected without the ability to enforce U.S. law on foreign land...."
Labels: choicepoint, identity theft, information breaches
Sunday, June 12, 2005
Keeping your data secret is up to you
An increasing portion of the mainstream media are picking up on privacy issues, mainly stemming from the string of breaches starting with ChoicePoint and culminating in the most recent CitiFinancial data loss. The Boston Globe is running a column by Michelle Singletary of the Washington Post that calls for legislation but also suggests that consumers become more proactive in protecting their personal information. The columnist shows one example from her own experience:
Keeping your data secret is up to you - The Boston Globe - Boston.com - Your Money - Business:"... For instance, I recently contracted to have an alarm system installed in my home. As I was filling out the sales agreement, I noticed a request for my Social Security number. I refused to divulge it. The salesman said it was a requirement. He said I ''had" to give it to him.
I unequivocally refused to divulge my number. A manager of the company called. He explained that it was needed to pull my credit score because we were signing up for a three-year monitoring service. He said it had been their experience that people with low credit scores often break the three-year contract.
Even if that was the case, I was appalled at the lack of security about my data from this company. By my rough estimate, from the time the salesman took my service agreement to his office, my data could have been exposed to at least half a dozen of the company's employees. In several of the recent data breaches, employees were doing the pilfering.
I was prepared to leave my home unprotected for the time being in the name of protecting my personal data.
Ah, but here's where it pays to be persistent about protecting your data.
The manager came up with a way to get my Social Security number without me actually giving it to him or anyone else at the company. In a three-way conference call, he phoned the credit bureau and when the automatic system asked for the customer's Social Security number, I punched it in. All he heard on his end was a beeping sound. In a few seconds he got my credit score without having to know my Social Security number.
So folks, it's up to us. We have to become our own data protectors. You may not win the battle all the time, but if you're fierce enough you can reduce the number of companies that have your information."
Labels: choicepoint, information breaches
Thursday, June 09, 2005
Public Disclosure of Personal Data Loss
Since the ChoicePoint fiasco, the hot topic in privacy is the question of public notification of security breaches. California has led the way on this and many state and federal legislators are looking to follow California's lead. The Federal Privacy Commissioner in Canada has suggested that notification should be done, but our privacy law contains no obligation (except for Ontario's Personal Health Information Protection Act).
Bruce Scheier always has interesting things to say and on this topic there's no exception:
Schneier on Security: Public Disclosure of Personal Data Loss:"... As a security expert, I like the California law for three reasons. One, data on actual intrusions is useful for research. Two, alerting individuals whose data is lost or stolen is a good idea. And three, increased public scrutiny leads companies to spend more effort protecting personal data.
Think of it as public shaming. Companies will spend money to avoid the PR cost of public shaming. Hence, security improves.
This works, but there's an attenuation effect going on. As more of these events occur, the press is less likely to report them. When there's less noise in the press, there's less public shaming. And when there's less public shaming, the amount of money companies are willing to spend to avoid it goes down...."
The attenuation effect may be true, but I don't think we've peaked on this yet. If you search Google News for "citigroup tape", you get well over 360 news stories about the incident. Eventually the media's interest will trail off, but I don't think it has happened yet.
Labels: breach notification, choicepoint, google, health information, information breaches, phipa, privacy, schneier
Tuesday, June 07, 2005
Data Aggregators: A Study on Data Quality and Responsiveness
PrivacyActivisim.org has conducted a study of the accuracy of information contained in the records of Choicepoint and Acxiom.
In light of the use the employers and others make of this information, the results are troubling....
Data Aggregators: A Study on Data Quality and Responsiveness:"...100% of the reports given out by ChoicePoint had at least one error in them. Error rates for basic biographical data (including information people had to submit in order to receive their reports) fared almost as badly: Acxiom had an error rate of 67% and ChoicePoint had an error rate of 73%. In other words, the majority of participants had at least one such significant error in their reported biographical data from each data broker...."
Thanks to Schneier on Security: Accuracy of Commercial Data Brokers for the link.
Labels: choicepoint, information breaches, schneier
Thursday, June 02, 2005
States Pass Privacy Laws
Network Magazine has an article on the eight states that have passed privacy laws similar to California's trail-blazing legislation:
Network Magazine's Weblog: States Pass Privacy Laws:"States Pass Privacy Laws
As of today, eight state legislatures have passed privacy legislation, largely in reaction to the recent, well-publicized privacy breach incidents at ChoicePoint, Axciom, Bank of America, LexisNexis, and others (and more states are debating such laws). This morning I read the eight states' laws to compare and contrast and see what, if any, unusual requirements they might contain (yes, maybe I do need to get a life). Although these state efforts may one day be superseded by a national law proposed by California Senator Dianne Feinstein based on her state's privacy law, the laws are all similar enough that if you understand the state laws, you'll be ready for the new national rules.
California's, Georgia's, Illinois', Washington's and Arkansas' bills are almost identical.
Florida's and North Dakota's bills are tougher than the others. They both have a section that cracks down on those who willfully and fraudulently use or create personal identification information -- Florida's sets minimum prison terms for offenders -- that hopefully won't apply to your company. The rest of these two bills mirror the other state laws, except that Florida's sets fines for violators (see below). North Dakota's act was declared an emergency measure and takes effect today; Florida's bill takes effect July 1.
Montana's bill has extra provisions for credit reporting bureaus and credit card companies, otherwise it is similar to California law. It takes effect March 1, 2006.
Illinois' rule applies to government agencies, whereas Florida specifically exempts them. Otherwise the state laws share the following common requirements...."
Labels: choicepoint, information breaches
Monday, May 16, 2005
Are security breaches on the rise or are we just hearing about them more often
The San Francisco Chronicle is citing the "ChoicePoint Effect", which means that more companies are willing to fess up when something goes awry with personal information. The article suggests that we aren't more data incidents, we're just hearing about them more often.
I'm not entirely sure this is the case. I have a feeling that the number of incidents has increased and we are hearing about it more often. ID theft is being perpetrated more and more often in recent years and I think that more criminals are seeking out personal information than they did before. A mugger would take your wallet and use your cards until you reported them stolen. Now, using the same stuff that's in your wallet, they're opening accounts in your name and committing a different species of crime. When personal information can be acquired in bulk, whether from dumpster diving or impersonating legitimate businesses, the sheer number of threats faced has to have increased and the number of incidents along with it.
The Chronicle article is here: Security breaches not on rise / Privacy watchdogs say incidents are being disclosed more often.
Labels: choicepoint, information breaches
Sunday, May 15, 2005
I want my name back!
The New York Daily News is running an overview of the growing crime of "identity theft." Not too much is news, but it does provide a good summary of how it happens and what sort of effect it can have on those whose information is compromised. Some stats:
New York Daily News - Home - I want my name back!:"BOOMING BIZ IN CRIME
- Annual ID theft cost: $48 billion
- Number of U.S. victims per year: 9.9 million
- Number of New York state ID theft complaints in 2003: 663,300
- Average thieves' profit setting up new accounts in a victim's name: $10,200
- Number of new accounts set up in the last year: 3.23 million
- Average thieves' profit using existing credit cards: $2,100
- Average time thieves use victims' ID: 3.2 months
- Average out-of-pocket expense per victim: $500
- Average loss to businesses per victim: $4,800
BUSY BEAVERS
Identities reported compromised by hackers or other unauthorized use of data banks in recent weeks:
- LexisNexis/Seisint ................................... 310,000 people
- DSW Shoe Warehouse .................... 1.4 million customers
- ChoicePoint Inc. ...................................... 145,000 people
- Polo Ralph Lauren ............................ 180,000+ customers "
Labels: choicepoint, identity theft, information breaches
Incident: Another data aggregator provides personal information to impostors
In an incident similar to the one that dragged ChoicePoint into the limelight, Merlin Information Systems has begun to notify nine thousand people that thier personal information (name, address, ssn) was obtained by somone who used fraudulent credentials to get access to the Merlin system. See Thief nets personal information from Kalispell company.
Labels: choicepoint, information breaches
Thursday, May 12, 2005
FindLaw's Modern Practice: The ChoicePoint Dilemma
Findlaw's most recent Modern Practice column is about the risks of data aggregators. Bob Barr's conclusion: Accept, but regulate, data aggregators: See FindLaw's Modern Practice. (Via Privacy Digest.)
Labels: choicepoint, information breaches
Friday, May 06, 2005
The Five Most Shocking Things About the ChoicePoint Debacle
Thanks to Bruce Schneier (Schneier on Security: Lessons of the ChoicePoint Theft) for the pointer to this very interesting essay from CSO (Chief Security Officer) magazine about the ChoicePoint and related privacy incidents: The Five Most Shocking Things About the ChoicePoint Debacle - CSO Magazine - May 2005.
Labels: choicepoint, information breaches, schneier
Thursday, May 05, 2005
Data execs tell House Committee they favour breach notification
InformationWeek > Customer Data Security > Execs Testify In Favor Of National Data-Security Law > May 4, 2005:"Executives from companies stung by losses or theft of customer information vowed Wednesday to do more to safeguard sensitive information and backed a federal law to require disclosure if customer data is compromised.
In prepared testimony for a hearing by the House Committee on Financial Services, executives from Bank of America, ChoicePoint, and LexisNexis supported legislation patterned after California's law requiring companies to notify customers about security breaches...."
Labels: breach notification, choicepoint, information breaches
Wednesday, May 04, 2005
Identity exposed: 5 Tips: What you can do to keep your employee information confidential.
I guess it's lists week. Earlier I pointed to an article about the seven tricks used by ID thieves (Seven techniques used by ID thieves). Now, CNN/Money has an article on the five things employees can do to protect their personal information:
5 Tips: Identity exposed - May. 4, 2005:"NEW YORK (CNN/Money) - We've reported to you about security breaches at ChoicePoint, Boston College, and LexisNexis. Now, the latest case of missing personal data turns out to be closer to home.
Time Warner, parent company of CNN/Money and CNN, announced Monday that 40 computer backup tapes containing the names and social security numbers of more than 600,000 current and former employees -- plus their dependents -- were lost.
...
Here are five tips on what you need to know about your employer and your personal information.
1. Employers hold the key.
Your social security number is the key to your credit. With that nine-digit number and your name, an identity thief can get access to your credit history, open credit cards in your name, even take out a mortgage posing as you.
...
2. Snoop around.
No kidding: your name and social security number could be on a checklist about the company picnic taped to the wall in the HR office. Maybe your HR department is a little more discreet. But do you know where your information is?
Take a cruise through the office. Do the timesheets in the open employee mailroom have names and social security numbers already printed on them? Are the file cabinets containing employee profiles unlocked? Does your ID card or health card have your SSN plastered on it?
...
3. Have a fit.
If your employer is guilty of being too casual with your personal information, go ahead, tell them they're wrong. Go tell your HR department you're concerned about the security of employee data.
...
4. Watch your back.
It's up to you to do what you can to protect yourself. The unfortunate thing is that most people don't.
...
5. Keep an eagle eye.
...
Worse, your employer is not the only one out there with access to your personal information. Your doctor, dentist, and utility provider might have your social security number because, well, they asked for it.
Don't be afraid to tell them "no" next time unless it's necessary. And when you give it up, ask them how seriously they take your security.
..."
Labels: choicepoint, health information, information breaches
Tuesday, May 03, 2005
Choicepoint continues its acquisition spree
Embattled ChoicePoint is continuing its long history of acquisitions, this time by buying EzGov and Magnify. See the press releases: ChoicePoint(R) Adds to Government Services; Expands by Acquiring EzGov Operations in the Americas, Caribbean and ChoicePoint(R) Acquires Magnify, Expanding Fraud Detection and Analytics Services.
Labels: choicepoint, information breaches
Thursday, April 28, 2005
Privacy and security are governace issues: ChoicePoint CEO Won't Discuss Breach
I would have thought that issues affecting share price and the future of the company are fair game at an annual general meeting, but the organizers of ChoicePoint's AGM didn't think so. A question about the high-profile breach that are leading to regulation of their industry were considered out of order, according to ABC News and the Associated Press:
ABC News: ChoicePoint CEO Won't Discuss Breach:"NEW YORK Apr 28, 2005 — ChoicePoint CEO Derek Smith refused to answer questions on Thursday about the security breach that allowed criminals to access the company's database, telling shareholders at the company's annual meeting that the matter was the subject of pending litigation.
"As we have previously disclosed, the company is continuing to investigate the recent fraudulent data access and other matters," Smith told about a dozen shareholders at the Waldorf-Astoria Hotel in Manhattan.
The Alpharetta, Ga.-based company announced in February that the personal information of 145,000 Americans may have been compromised when thieves posing as legitimate small business customers gained access to its database. Authorities say at least 750 people were defrauded in the scam. The scandal has fueled consumer advocates' calls for federal oversight of the loosely regulated data-brokering business, and Capitol Hill hearings are likely soon on the issue.
...
Smith and ChoicePoint President Douglas Curling earned $16.6 million from ChoicePoint stock sales after the company learned last fall of the security breach and before that was made public on Feb. 15.
During Wednesday's brief meeting, the shareholders voted in four new directors and approved the appointment of Deloitte & Touche as the company's independent auditor.
After reading prepared remarks, Smith answered written questions submitted by shareholders. A question relating to the security breach was deemed inappropriate and was not read aloud...."
Labels: choicepoint, information breaches
Wednesday, April 20, 2005
Privacy from the trenches
Scott Granneman, in The Register, joins the chorus of those calling for stronger privacy laws in the United States:
Privacy from the trenches | The Register:"... I hate to involve the government unless it's necessary, but I think something's got to give here. We can't rely on companies, schools, and organizations policing themselves. That's obviously a terrible failure. We need federal legislation to mandate that organizations that experience data thefts must notify those affected by the breach in a timely manner. As Mark Rasch stated earlier this week, recent legislation was passed that requires this for all financial institutions in the U.S., but all other companies are still off the hook. Right now, a few states have such a law -- California is one, which is why ChoicePoint even had to make its embarrassing revelation in the first place -- but there is no federal, all-encompassing requirement for anything but financial institutions (and even that law is very recent). This needs to change, and soon. Other states have proposed legislation, but it varies from state-to-state. A new federal law would be a great start. Right after that, a few class-action lawsuits against particularly egregious carelessness might also wake companies and schools up to the necessity of protecting data. Again, I don't like bringing in the lawyers, but to paraphrase the great Dr. Samuel Johnson, 'Depend upon it, sir, when a man knows he is to be sued in a fortnight, it concentrates his mind wonderfully.'..."
Labels: choicepoint, information breaches
ChoicePoint Division Changes Tack, Notifies Individuals of Use of their Information
Wired News is reporting that a recently-acquired division of embattled ChoicePoint is changing its practices by notifying individuals if a negative criminal records check has been disclosed:
Wired News: ChoicePoint Division Changes Tack:"...On Tuesday, the company sent an e-mail to customers announcing that it is implementing 'a new compliance policy.' Effective April 25, whenever a customer runs a background search on someone through the Rapsheets database for employment- or volunteer-screening purposes and the search unearths a criminal record for that person, Rapsheets will automatically notify the person and provide him or her with a copy of the background report and the name and address of the organization that requested it...."
Labels: choicepoint, information breaches
![]()

The Canadian Privacy Law Blog is licensed under a
Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Canada License.




